Find, fix, and prevent vulnerabilities
Содержание:
- Verifying Scan Target Ownership (Acunetix Online only)
- How does network vulnerability scanning work?
- Gareth Davies for Darknet.org.uk Reviews Acunetix
- (30) ★★★★½ Nikto (#14, 2)
- Acunetix Vulnerability Management
- (4) ★★★★½ SAINT (#110, 19)
- Version 13 (build 13.0.200624118 – Windows and Linux) 24th June 2020
- SQLMap
- Become a Beta tester
- Features to consider
- Minimum System Requirements
- Zed Attack Proxy
- Conclusion
- Dr.Web 8.00.0(1) [2013, Антивирус] RU
- Excluded Hours
- Introduction
- Caveats
- What Causes Security Vulnerabilities?
- Install the Main Installation
- 3 more network vulnerability scanners
Verifying Scan Target Ownership (Acunetix Online only)
Once you create a new Target, you will be asked to verify ownership of the Target. Target verification will depend on the type of scans that you intend to launch against the Target.
In summary, web vulnerability scans require a unique verification file to be present in the root of the web server before a scan starts. This is required for all your Targets against which you wish to run web scans.
Network vulnerability scans require that we verify your account details; a one-time process where you may be contacted by an Acunetix representative.
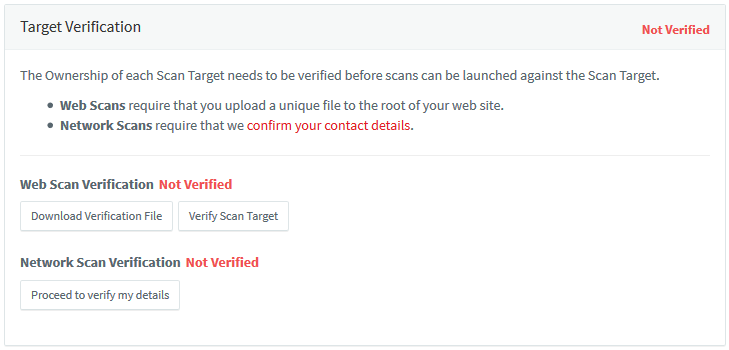 Screenshot — Scan Target Verification required
Screenshot — Scan Target Verification required
Web Scan Verification
Web scan verification is a 3 step process.
- Download the unique verification file assigned to your new Target.
- Upload the verification file to the root of the site (using FTP for example).
- From the configuration of the Target in Acunetix Online, click on ‘Verify Scan Target’ to complete the verification process.
Note: The verification file needs to be kept in the root of the site, since Acunetix Online will check the verification file each time it scans the server.
Network Scan Verification
- For network scans you will need to verify that your account details are correct, and request verification of your account by an Acunetix representative.
- From within the configuration of your scan target, in the Network Scan Verification, click ‘Proceed to verify my details’, or you can go directly to Account Settings > Profile.
- Confirm that your account details are correct, and update as needed.Screenshot — Verify account details
- From within the Account Verification section, you can request the verification of your account details.
- You will immediately receive an automatic call to the phone number specified, and will be given a one time code. You will need to enter this code into Acunetix as part of the account verification process.
- An Acunetix representative may get in touch with you within 24 hours to complete the verification.
- Once your account details have been verified, you can launch network vulnerability scans on all your scan targets.
Contact us at support@acunetix.com if you require help with the verification process.
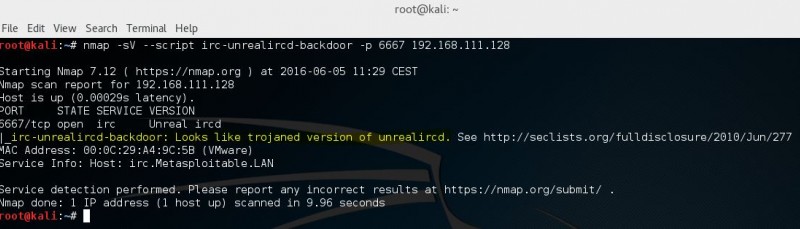
How does network vulnerability scanning work?
Vulnerability scanning software relies on a database of known vulnerabilities and automated tests for them. A limited scanner will only address a single host or set of hosts running a single operating system platform. A comprehensive scanner scans a wide range of devices and hosts on one or more networks, identifying the device type and operating system, and probing for relevant vulnerabilities with lesser or greater intrusiveness.
A scan may be purely network-based, conducted from the wider internet (external scan) or from inside your local intranet (internal scan). It may be a deep inspection that is possible when the scanner has been provided with credentials to authenticate itself as a legitimate user of the host or device.
Gareth Davies for Darknet.org.uk Reviews Acunetix
“Acunetix Online Vulnerability Scanner is responsive, scalable and centralised with unmatched deep crawling and scanning capabilities. If you compare it to the on-premise solution, it’s simple to use, there’s no maintenance (as its cloud based) and it’s very competitively priced.
Overall I think it’s a great tool and I’m glad to see a company like Acunetix, who has a great software scanner moving more into a SaaS (Software-as-a-Service) style offering. It suits the mobile pen-testing consultant a lot more, especially with agile teams working together the old methods of generating reports with software on each engineer laptop was cumbersome and hard to scale.”
(30) ★★★★½ Nikto (#14, 2)
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.
Latest release: version 2.1.4 on Feb. 20, 2011 (9 years, 6 months ago).
Acunetix Vulnerability Management
Acunetix is an automated web application security testing tool that audits your web applications by checking for vulnerabilities like SQL Injection, Cross site scripting and other exploitable vulnerabilities. In general, Acunetix scans any website or web application that is accessible via a web browser and uses the HTTP/HTTPS protocol.
Acunetix offers a strong and unique solution for analyzing off-the-shelf and custom web applications including those utilizing JavaScript, AJAX and Web 2.0 web applications. Acunetix has an advanced crawler that can find almost any file. This is important since what is not found cannot be checked.
How Acunetix Works
Acunetix works in the following manner:
- Acunetix DeepScan analyses the entire website by following all the links on the site, including links which are dynamically constructed using JavaScript, and links found in robots.txt and sitemap.xml (if available). The result is a map of the site, which Acunetix will use to launch targeted checks against each part of the site.
- If Acunetix AcuSensor Technology is enabled, the sensor will retrieve a listing of all the files present in the web application directory and add the files not found by the crawler to the crawler output. Such files usually are not discovered by the crawler as they are not accessible from the web server, or not linked through the website. Acunetix AcuSensor also analyses files which are not accessible from the internet, such as web.config.
- After the crawling process, the scanner automatically launches a series of vulnerability checks on each page found, in essence emulating a hacker. Acunetix also analyses each page for places where it can input data, and subsequently attempts all the different input combinations. This is the Automated Scan Stage. If the AcuSensor Technology is enabled, a series of additional vulnerability checks are launched against the website. More information about AcuSensor is provided in the following section.

- The vulnerabilities identified are shown in the Scan Results. Each vulnerability alert contains information about the vulnerability such as POST data used, affected item, HTTP response of the server and more.
- If AcuSensor Technology is used, details such as source code line number, stack trace or affected SQL query which lead to the vulnerability are listed. Recommendations on how to fix the vulnerability are also shown.
- Various reports can be generated on completed scans, including Executive Summary report, Developer report and various compliance reports such as PCI DSS or ISO 270001.
(4) ★★★★½ SAINT (#110, 19)
SAINT is a commercial vulnerability assessment tool. Like Nessus, it used to be free and open source but is now a commercial product. Unlike Nexpose, and QualysGuard, SAINT runs on Linux and Mac OS X. In fact, SAINT is one of the few scanner vendors that don’t support (run on) Windows at all.
Latest release: version 7.13 on May 18, 2012 (8 years, 3 months ago).
11 tools
Categories
- Antimalware (3)
- Application-specific scanners (3)
- Web browser–related (4)
- Encryption tools (8)
- Debuggers (5)
- Firewalls (2)
- Forensics (4)
- Fuzzers (4)
- General-purpose tools (8)
- Intrusion detection systems (6)
- Packet crafting tools (6)
- Password auditing (12)
- Port scanners (4)
- Rootkit detectors (5)
- Security-oriented operating systems (5)
- Packet sniffers (14)
- Vulnerability exploitation tools (11)
- Traffic monitoring tools (10)
- Vulnerability scanners (11)
- Web proxies (4)
- Web vulnerability scanners (20)
- Wireless tools (5)
Version 13 (build 13.0.200624118 – Windows and Linux) 24th June 2020
New Features
- Introduced support for GraphQL
- Introduced support for OAuth2.0
- GraphQL files can be used as Import Files
- New Comprehensive Report, which includes the HTTP Response in the HTML version of the report
- HTTP Response uses syntax highlighting for improved readability
- Scans can now be restricted to paths/locations in import files
- User can choose which columns to show in all the Acunetix lists
- UI saves columns selected for each page / user (applies to Targets, Vulnerabilities, Scans and Reports)
- UI saves number of items to show on each page / user (applies to Targets, Vulnerabilities, Scans and Reports)
- UI saves sorting order for each page / user (applies to Targets, Vulnerabilities, Scans and Reports)
New Vulnerability Checks
- New check for vBulletin 5.6.1 (and earlier) nodeId SQL injection
- New check for Cmd hijack vulnerability
- New check for PHP opcache-gui publicly accessible
- New check for
- New check for Laravel Health Monitor publicly accessible
- New check for Laravel Health Horizon publicly accessible
- New check for Laravel Health LogViewer publicly accessible
- New check for Laravel Health Telescope publicly accessible
- New check for Laravel Ignition Reflected Cross-Site Scripting
- New check for Laravel framework weak secret key
- New check for HTML Attribute Injection
- New check for Clockwork PHP dev tool enabled
- New check for PHP Debug Bar enabled
- New check for Broken Link Hijacking
- New checks for Cookie misconfigurations leading to security issues
- New vulnerabilities for WordPress Core, WordPress plugins, Joomla and Drupal
Updates
- Targets with Manual Intervention cannot have a Business Logic Recording
- Changed vulnerability name filter to use search as you type
- Scans will start reporting pages that require HTTP Authentication
- Acunetix UI notifications have been changed as follows:
- Moved to bottom right of Acunetix UI
- Stay longer on the page
- Can be closed by the user
- Increased name length limit of import files to 128 characters
- User can optionally specify the address to be used for Auto-login. This is useful for SSO login pages
- The scanner will try to connect to the address of the target before aborting the scan after 25 consecutive network errors
- Targets can be deleted and replaced on the license anniversary
Fixes
- Fixed: The vulnerability name filter did not always show all vulnerabilities
- Fixed incorrect error handling message when disabling the proxy settings
- Hide Business Logic Recorder for Network Only targets
- Fixed: Acunetix Online was showing an ID as the name of some network vulnerabilities
- Fixed: Acunetix Online was not always showing the HTTP Response for some vulnerabilities
- Fixed: Acunetix Online was not showing the number of licensed Targets
- Fixed issue causing paths of ignored files to be ignored too
- Fixed LSR issue on Safari browser
- Fixed issue caused when the LSR and BLR are used on certain sites
- Various minor fixes to the UI
- Fixed false positives in over 25 vulnerability checks
SQLMap
SQLMap is another popular open-source penetration testing tool. It automates the process of finding and exploiting SQL injection vulnerabilities in a website’s database. It has a powerful detection engine and many useful features. This way, a penetration tester can easily perform an SQL injection check on a website.
It supports a range of database servers including MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase and SAP MaxDB. It offers full support for six kinds of SQL injection techniques: time-based blind, Boolean-based blind, error-based, UNION query, stacked queries and out-of-band.
Access the source code on GitHub here.
Download SQLMap here.
Become a Beta tester
Are you a security researcher who’s passionate about web security? Do you want to stay current with the latest cutting-edge web security scanning technologies? Contact us at beta@acunetix.com to learn more. (Requests are subject to approval)
Acunetix customers who already own an Enterprise or Consultant license with a valid maintenance agreement are automatically eligible to participate as beta testers.
The Acunetix WVS Version 8 user manual is available in PDF Format.
Get the latest content on web security in your inbox each week.
THE AUTHOR
Acunetix
Acunetix developers and tech agents regularly contribute to the blog. All the Acunetix developers come with years of experience in the web security sphere.
Features to consider
When choosing a vulnerability scanner there are many features to evaluate.
- Is the scanner network-based, doing host/device discovery and target profiling?
- What is the range of assets it can scan – hosts, network devices, web servers, virtual machine environments, mobile devices, databases? Does that fit your organization’s needs?
- Is its vulnerability database comprehensive and a good match for your network’s platforms? Does the database automatically receive a regular feed of updates?
- Is the scanner accurate in your environment? Does it swamp you with uninformative low-level results? What is the incidence of false positives and false negatives? (A false positive entails wasted effort to investigate, and a false negative means an undetected risk.)
- Is the scanner reliable and scalable?
- Are the scanner’s tests unnecessarily intrusive? Does scanning impact hosts/devices thereby slowing performance and potentially crashing poorly-configured devices?
- Can you set up scheduled scans and automated alerts?
- Does it provide canned policies (e,g. for particular compliance regimes)? Can you define your own policies?
- Are scan results easy to understand? Can you sort and filter? Can you visualize trends over time? Does it provide useful guidance about prioritization?
- Does it help with remediation? Are the instructions clear? How about automated remediation through scripting? Does it provide, or integrate with, automated software updating services to install service packs and patches?
- What is the range of canned reports it provides, and what is their quality? Does it provide any compliance reports you need? Can you easily define your own report formats?
Minimum System Requirements
- Microsoft Windows 8.1 or Windows 2012 R2 and later
- MacOS Mojave and MacOS Catalina
- Ubuntu Desktop/Server 16.0.4 LTS or higher
- Suse Linux Enterprise Server 15
- openSUSE Leap 15.0 and 15.1
- Kali Linux versions 2019.1 and 2020.1
- CentOS 8 Server and Workstation (with SELinux disabled)
- RedHat 8 (with SELinux disabled)
- We are actively testing other Linux distributions. Please let us know if you have requests for specific distros.
- CPU: 64 bit processor
- System memory: minimum of 2 GB RAM
- Storage: 1 GB of available hard-disk space. This does not include the storage required to save the scan results — this will depend on the level of usage of Acunetix.
Zed Attack Proxy
Zed Attack Proxy is also known as ZAP. This tool is open-source and is developed by OWASP. It is available for Windows, Unix/Linux and Macintosh platforms.
I personally like this tool. It can be used to find a wide range of vulnerabilities in web applications. The tool is very simple and easy to use. Even if you are new to penetration testing, you can easily use this tool to start learning penetration testing of web applications.
These are the key functionalities of ZAP:
- Intercepting proxy
- Automatic scanner
- Traditional but powerful spiders
- Fuzzer
- Web socket support
- Plug-n-hack support
- Authentication support
- REST-based API
- Dynamic SSL certificates
- Smartcard and client digital certificates support
You can either use this tool as a scanner by inputting the URL to perform scanning, or you can use this tool as an intercepting proxy to manually perform tests on specific pages.
Download ZAP here.
Conclusion
Vulnerability scanning – and in fact, vulnerability management – is one aspect of protecting your network. Scanners can only detect vulnerabilities that already have tests implemented. You also need to develop a sense of your network’s normal behaviors, via bandwidth monitoring and analysis tools, particularly tools that let you specify automated alerts. When you sense an anomaly and must investigate, network analyzers and packet sniffers are key tools. And there are many other kinds of security tools for the network administrator.
Vulnerability scanning software is essential to help defend your network. There are multiple free options to try out; the right one for your organization is based on your needs, funding, and expertise – or willingness to learn.
Relevant: Best Angry IP Scanner Alternatives
Dr.Web 8.00.0(1) [2013, Антивирус] RU
Год выпуска: 2013Жанр: АнтивирусРазработчик: «Доктор Веб»Сайт разработчика: http://drweb.com/Язык интерфейса: РусскийПлатформа: AndroidСистемные требования: Android 2.1 и выше Описание: Dr.Web — всесторонняя защита от вирусов, спама и опасных веб-сайтов! Защитите ваше мобильное устройство от вирусов и спама с помощью популярного антивируса от «Доктор Веб» — ведущего российского разработчика средств информационной безопасности. Антивирус Dr.Web обеспечит вас и ваше мобильное устройство постоянной антивирусной защитой, интеллектуальной фильтрацией звонков и СМС, а также инструментами для …
Программы / КПК и Мобилы / На базе Android
Подробнее
Excluded Hours
There are times when you do not want to scan a Target. For example, you might want to scan your site during your workday so you can monitor the site while it is being scanned. Alternatively, you can scan your web application during the weekend when nobody is using it.

Screenshot — Excluded hours list
Excluded hours allow you to configure the times when no scans should be done by Acunetix. The default excluded hours profile is assigned to all new Targets, however this can be changed to a different excluded hours profile for each Target. You can also create your custom excluded hours profile if needed.

Screenshot — Edit an excluded hours profile
Note: Any scans that are running at the start or an excluded hours period will be stopped. Any scans that are scheduled to start during an excluded hour period will be delayed till after the excluded hour period.
Introduction
In the past, many popular websites have been hacked. Hackers are active and always trying to hack websites and leak data. This is why security testing of web applications is very important. And this is where web application security scanners come into play.
A web application security scanner is a software program which performs automatic black-box testing on a web application and identifies security vulnerabilities. Scanners do not access the source code; they only perform functional testing and try to find security vulnerabilities. Various paid and free web application vulnerability scanners are available.
In this post, we are listing the best free open-source web application vulnerability scanners. I’m adding the tools in random order, so please do not think it is a ranking of tools.
I am only adding open-source tools which can be used to find security vulnerabilities in web applications. I am not adding tools to find server vulnerabilities. And do not confuse free tools and open-source tools! There are various other tools available for free, but they do not provide source code to other developers. Open-source tools are those which offer source codes to developers so that developers can modify the tool or help in further development.
These are the best open-source web application penetration testing tools.
Caveats
The vulnerability scanner is only one source of information and is not a replacement for having knowledgeable staff.
Like many network administration tools targeted at enterprises, a high-end vulnerability scanner tends to be expensive. Good no-cost options are available, but many are limited in the size of the network they’ll handle, and all entail the cost of paying staff to learn the tool, install and configure it, and interpret its results. Thus, you should evaluate whether paying for more automation and support may be cheaper in the long run.
Installing a scanner can be complicated, and likely the scanner will initially grind for a few hours to fetch updates to its vulnerability database and preprocess them. Also, depending on the number of hosts and the depth of the scan selected, a given scan can also take hours.
What Causes Security Vulnerabilities?
There are countless ways bad actors could compromise a network and steal data. That said, there are common security vulnerabilities to watch out for. Not every network scanning tool will address all these concerns, but you should look for software to help you prioritize some or all of the following threats.
- Network structure – Too many business networks are essentially “open,” which means once an unauthorized user gains access, they have access to all parts of the network. This vulnerability can be prevented with better network segmentation and management of user group privileges.
- Unknown devices – Unidentified or unmanaged assets on your network are never good news. It’s important to make sure only approved devices have access to your ports.
- Account abuse – Unfortunately, insiders sometimes abuse their privileges, causing purposeful or inadvertent leaks of sensitive information, or the misconfiguration of programs, causing additional security holes. Furthermore, admins might allow default credentials, leave unused users or groups in the system, or assign incorrect privileges, all of which pose a security risk.
- Web configuration errors – To ensure website application security, you need to watch out for issues like distributed denial-of-service attacks, HTTP misconfigurations, expired SSL/TLS certificates, and insecure code.
- Security feature configurations – How you manage your security settings and infrastructure could open risks. To avoid vulnerabilities, watch for firewall or OS misconfigurations.
- Third-party applications – There’s a reason no one uses Java anymore. Too many third-party applications open security holes, whether because of how they’re built or how they’re downloaded and implemented. In addition to avoiding these applications, watch out for suspicious downloads, insecure remote desktop sharing software, and software nearing the end of its life.
- Missing updates – One major cause of security issues on networks is basic errors in software and firmware configuration or cases where configuration levels become uneven across the network. Similarly, it’s all too easy to fall behind on updating and patching devices and programs, even if patches are available. Hackers can quickly exploit these gaps.
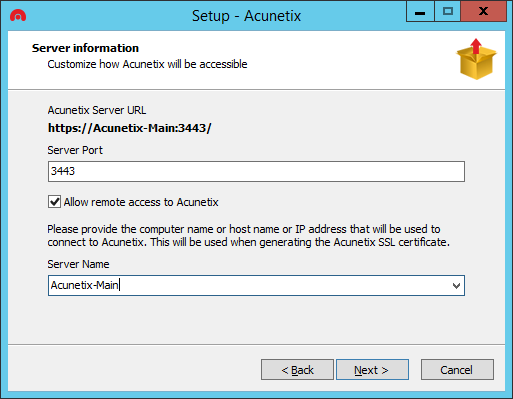
Install the Main Installation
The Main Installation is the installation which will be used to control all the Engines. It is also the installation which will host the Acunetix configuration database, and from which all the Acunetix settings will be configured. The Scanning Engine of this installation will also be used to perform security scans.
Proceed with installing the Main installation by double clicking on the Acunetix installation. In the “Server information” page, you need to enable “Allow remote access to Acunetix”, and configure a Server Name that is reachable from all the machines running the Scanning Engines.
3 more network vulnerability scanners
If the eight best network scanners in our list don’t quite fit your needs, you might consider one of these alternatives, which are “bubbling under” the leaders.
Tripwire Enterprise
The Tripwire Enterprise package of security vulnerability network checks is not free but you can try a demo. However, you can get it on a free trial. This service not only scans your network for anomalies on demand but runs in real-time, alerting you to any configuration or data changes on your network and enforcing change control.
Qualys FreeScan
Qualys FreeScan is an online service that examines a server or network for security weaknesses. It will identify your server software and check that they are up to the latest patches. The scan will also search for infection or intruder activity. This service is not free forever, after 10 scans you have to pay.
Netsparker
Netsparker is available as an on-premises application or as a cloud service. This is a costly option, which is the main reason that it does not appear in the main list of this guide. The vulnerability scanner is aimed at web servers and authenticates the activities of all applications that operate to support a web-based enterprise.