Packet capture library for windows
Содержание:
- Source Code Distribution
- 13: Game of Death
- Snowden
- Justice League: Doom
- Introduction
- Conclusion
- Определяем название и версию сервиса на порте
- Nmap In The Movies
- How To Scan Ports with Nmap
- Ocean’s 8
- Matrix Reloaded
- Downloading and Installing Npcap Free Edition
- Microsoft Windows binaries
- Install Nmap
- История
- 3rd Party Docs
- The Girl with the Dragon Tattoo
- Определяем имя и версию ОС
- Broken Saints
- Nmap Book
- Nmap Network Scanning
- Nmap参考指南(Man Page)
- 描述
- Базовые возможности
- Linux RPM Source and Binaries
Source Code Distribution
This is the traditional compile-it-yourself format. The Nmap
tarball compiles under Linux, Mac OS X, Windows, and many UNIX
platforms (Solaris, Free/Net/OpenBSD, etc.) It includes Zenmap, the
GUI frontend.
Detailed Linux/BSD/Solaris compilation instructions and options are provided here, though this usually does the trick:
bzip2 -cd nmap-7.80.tar.bz2 | tar xvf - cd nmap-7.80 ./configure make su root make install
Most Windows users install with our , but we also provide .
Most Mac OS X users install with our , but we also provide .
If you are compiling Nmap anyway, you might prefer to get the very latest code from rather than downloading a tarball here.
Latest stable Nmap release tarball: nmap-7.80.tar.bz2 (or gzip compressed)
13: Game of Death
Nmap was used in the acclaimed Thai thriller 13:
Game of Death
(Wikipedia,
IMDB, Amazon), also known as «13 Beloved» and «13 game sayawng». This movie follows the story of a man given the chance to complete 13 challenges to win $100,000,000. Successive challenges become increasingly intense, dangerous, illegal, degrading, and grotesque. What would you do for $100 million? Eventually one of his sysadmin friends gets worried about him and she demonstrates Nmap hacking skills by breaking into the twisted game’s website (longer summary).
We have received
an AVI video (5MB)
of the scene, and also numerous
screenshots.

Thanks to Tazman for first notifying me of the scene, and to Laga Mahesa and Ithilgore for sending screenshots.
Snowden
Oliver Stone’s 2016 Snowden film (Wikipedia, IMDB, Amazon) dramatizes Edward Snowden’s massive leak of classified documents revealing NSA widespread surveillance of U.S. citizens. In one early scene, Snowden is given a network security challenge at a CIA training class which is expected to take 5 to 8 hours. But with the help Nmap and a custom Nmap NSE script named ptest.nse, Snowden stuns the professor by completing everything in 38 minutes! Nmap’s distinct tabular output is visible on other students’ screens too, though we may have to wait for the 4K resolution film release to read the exact text. Here are a couple screen shots from the Nmap scenes:
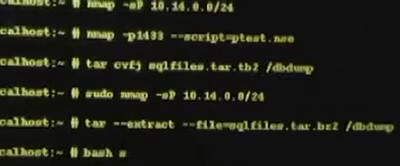

And here is the whole trailer (with Nmap glimpse at 34 seconds in):
Congratulations to Prabesh Thapa from Nepal for being first to discover and report the Nmap scenes!
Justice League: Doom
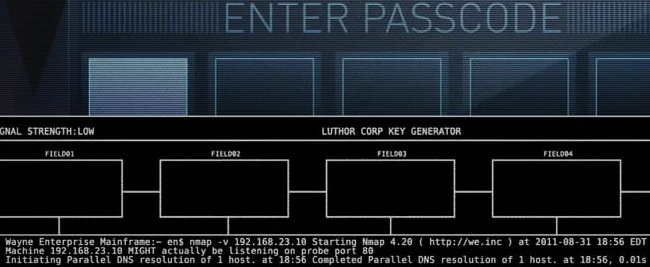
Nmap is used in the opening credits of
Justice League: Doom (Wikipedia, IMDB, Amazon). This 2012 animated superhero film features Batman, Superman, Wonder Woman, and Green Lantern battling a team of supervillains. Thanks to Spencer Davenport for catching this and sending screenshots. It is interesting that in most cases (but not all), they changed the Nmap URL (http://nmap.org) in the Nmap output to http://we.inc (Wayne Enterprises). Also, they ran the command in August 2011 using a version of Nmap (4.20) from 2006. I realize that Batman has a lot of important and heroic work to do, but surely he can spare 5 minutes to download and install the latest version of Nmap!
Introduction
Scanning, as a method for discovering exploitable communication channels, has
been around for ages. The idea is to probe as many listeners as possible, and
keep track of the ones that are receptive or useful to your particular need.
Much of the field of advertising is based on this paradigm, and the «to current
resident» brute force style of bulk mail is an almost perfect parallel to what
we will discuss. Just stick a message in every mailbox and wait for the
responses to trickle back.
Scanning entered the h/p world along with the phone systems. Here
we have this tremendous global telecommunications network, all
reachable through codes on our telephone. Millions of numbers are
reachable locally, yet we may only be interested in 0.5% of these
numbers, perhaps those that answer with a carrier.
The logical solution to finding those numbers that interest us is
to try them all. Thus the field of «wardialing» arose. Excellent
programs like Toneloc were developed to facilitate the probing of
entire exchanges and more. The basic idea is simple. If you dial a
number and your modem gives you a CONNECT, you record it. Otherwise
the computer hangs up and tirelessly dials the next one.
While wardialing is still useful, we are now finding that many of
the computers we wish to communicate with are connected through
networks such as the Internet rather than analog phone dialups.
Scanning these machines involves the same brute force technique. We
send a blizzard of packets for various protocols, and we deduce which
services are listening from the responses we receive (or don’t
receive).
Conclusion
Understanding port configuration and how to discover what the attack vectors are on your server is only one step to securing your information and your VPS. It is an essentail skill, however.
Discovering which ports are open and what information can be obtained from the services accepting connections on those ports gives you the information that you need to lock down your server. Any extraneous information leaked out of your machine can be used by a malicious user to try to exploit known vulnerabilities or develop new ones. The less they can figure out, the better.
<div class=“author”>By Justin Ellingwood</div>
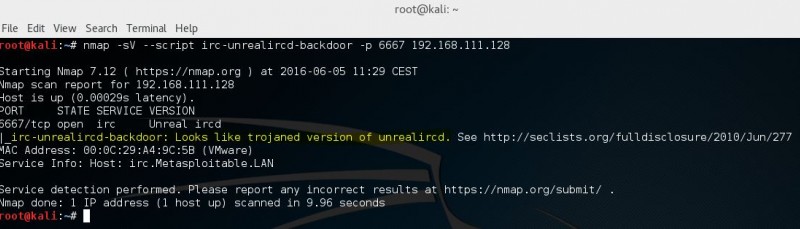
Определяем название и версию сервиса на порте
Одна из интересных особенностей Nmap в том, что он способен не только определить состояние порта (открыт, закрыт, фильтруется), но и идентифицировать имя демона/службы на этом порте, а в некоторых случаях даже его версию. Для этого Nmap может применять несколько разных техник, например подключиться к порту 80 и послать HTTP-запрос для идентификации имени и версии веб-сервера либо использовать информацию о том, как сервис отвечает на те или иные пакеты и запросы.
Все правила идентификации служб и их версий определены в файле <span class=»nobr»>, а заставит Nmap их применить флаг :
Причем есть возможность даже усилить попытки Nmap определить службу с помощью флага :
Однако обычно это не повышает качество распознавания.
Nmap не смог определить версию HTTP-сервера, но узнал его имя
Nmap In The Movies
For reasons unknown, Hollywood has decided that Nmap is the
tool to show whenever hacking scenes are needed. At least it is a lot
more realistic than silly 3D animation approach used in many previous
movies (e.g. «hacking the Gibson» on Hackers, or the much worse
portrayals on Swordfish). We always like to see Nmap in the movies,
so we have catalogued known instances here.
Update (April 21, 2020): I (Fyodor) am way behind on adding new movies. Sorry about that! You are still welcome and encouraged to submit movies as described above as long as you understand that the prize may have already been awarded to an earlier submitter for movies that aren’t yet on this page. I’ll remove this update once I’m caught up. Cheers!
This page only covers movies, we have a separate page coving news articles, reviews, books, and popular culture references.
How To Scan Ports with Nmap
Nmap can reveal a lot of information about a host. It can also make system administrators of the target system think that someone has malicious intent. For this reason, only test it on servers that you own or in situations where you’ve notified the owners.
The nmap creators actually provide a test server located at:
This, or your own VPS instances are good targets for practicing nmap.
Here are some common operations that can be performed with nmap. We will run them all with sudo privileges to avoid returning partial results for some queries. Some commands may take a long while to complete:
Scan for the host operating system:
<pre>
sudo nmap -O <span class=“highlight”>remote_host</span>
</pre>
Skip network discovery portion and assume the host is online. This is useful if you get a reply that says “Note: Host seems down” in your other tests. Add this to the other options:
<pre>
sudo nmap -PN <span class=“highlight”>remote_host</span>
</pre>
Specify a range with “-” or “/24” to scan a number of hosts at once:
<pre>
sudo nmap -PN <span class=“highlight”>xxx.xxx.xxx.xxx-yyy</span>
</pre>
Scan a network range for available services:
<pre>
sudo nmap -sP <span class=“highlight”>networkaddressrange</span>
</pre>
Scan without preforming a reverse DNS lookup on the IP address specified. This should speed up your results in most cases:
<pre>
sudo nmap -n <span class=“highlight”>remote_host</span>
</pre>
Scan a specific port instead of all common ports:
<pre>
sudo nmap -p <span class=“highlight”>portnumber</span> <span class=“highlight”>remotehost</span>
</pre>
To scan for TCP connections, nmap can perform a 3-way handshake (explained below), with the targeted port. Execute it like this:
<pre>
sudo nmap -sT <span class=“highlight”>remote_host</span>
</pre>
To scan for UDP connections, type:
<pre>
sudo nmap -sU <span class=“highlight”>remote_host</span>
</pre>
Scan for every TCP and UDP open port:
<pre>
sudo nmap -n -PN -sT -sU -p- <span class=“highlight”>remote_host</span>
</pre>
A TCP “SYN” scan exploits the way that TCP establishes a connection.
To start a TCP connection, the requesting end sends a “synchronize request” packet to the server. The server then sends a “synchronize acknowledgment” packet back. The original sender then sends back an “acknowledgment” packet back to the server, and a connection is established.
A “SYN” scan, however, drops the connection when the first packet is returned from the server. This is called a “half-open” scan and used to be promoted as a way to surreptitiously scan for ports, since the application associated with that port would not receive the traffic, because the connection is never completed.
This is no longer considered stealthy with the adoption of more advanced firewalls and the flagging of incomplete SYN request in many configurations.
To perform a SYN scan, execute:
<pre>
sudo nmap -sS <span class=“highlight”>remote_host</span>
</pre>
A more stealthy approach is sending invalid TCP headers, which, if the host conforms to the TCP specifications, should send a packet back if that port is closed. This will work on non-Windows based servers.
You can use the “-sF”, “-sX”, or “-sN” flags. They all will produce the response we are looking for:
<pre>
sudo nmap -PN -p <span class=“highlight”>portnumber</span> -sN <span class=“highlight”>remotehost</span>
</pre>
To see what version of a service is running on the host, you can try this command. It tries to determine the service and version by testing different responses from the server:
<pre>
sudo nmap -PN -p <span class=“highlight”>portnumber</span> -sV <span class=“highlight”>remotehost</span>
</pre>
There are many other command combinations that you can use, but this should get you started on exploring your networking vulnerabilities.
Ocean’s 8
Ocean’s 8 (Wikipedia, IMDB, Amazon) is a 2018 comedy heist film starring Sandra Bullock, Rihanna, Cate Blanchett, and Anne Hathaway that continues the series started by Ocean’s Eleven in 2001. Rihanna plays the film’s main hacker, Nine Ball. She uses Nmap in many scenes to compromise people and companies responsible for guarding the $150 million diamond necklace they want to steal. Nmap is normally shown in the background as context to her hacks rather than taking the leading role.
In this screen (full version), Nmap is shown in the two screens on the right while they are 3D-scanning their target necklace on the left:
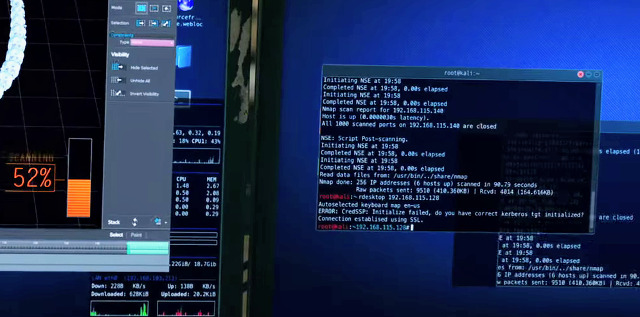
And here is the whole gang gathered together to (presumably) analyze their Nmap results (image is from here):

Even the movie trailer has a glimpse of Nmap at 1:50:
For more details on the Ocean’s 8 hacking scenes themselves, see security researcher Samy Kamkar’s analysis.
Congratulations to Alejandro Hernandez for being first to discover and report the Nmap scenes!
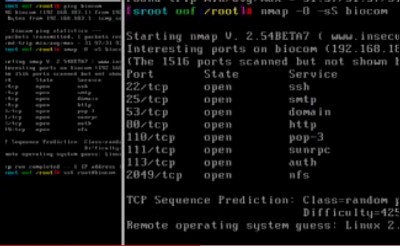
Matrix Reloaded
While Nmap had been used in some previous obscure movies, it was
The Matrix Reloaded (Wikipedia, IMDB, Amazon) which really turned Nmap into a movie star!
We have all seen many movies like Hackers which pass off ridiculous 3D animated eye-candy scenes as hacking. So Fyodor was
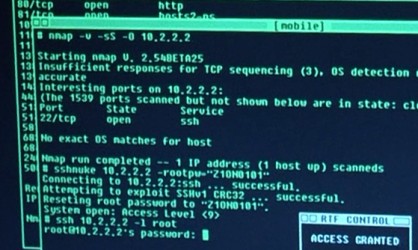
shocked to find that Trinity does it properly in The Matrix Reloaded.
Needing to hack the city power grid, she whips out Nmap version
2.54BETA25, uses
it to find a vulnerable SSH server, and then proceeds to exploit it
using the SSH1
CRC32 exploit from 2001. Shame on the city for being vulnerable (timing notes).
A video of the exploit
is available on
YouTube or
as matrix-nmap.mp4.
Click on the following thumbnails for higher resolution or
view more pictures here.

Updates:
- News articles about the Matrix cameo:
BBC,
Slashdot,
SecurityFocus,
Silicon.Com - JWZ has added this cracking scene as an XScreenSaver 4.10 Easter Egg — run ‘xmatrix -small -crack’.
- Several people have submitted matrix-themed banners to the propaganda gallery. Feel free to use any of these to link to Insecure.org — we appreciate it!
- The UK’s Scotland Yard Computer Crime Unit and the British Computer Society have put out a joint warning that «Viewers of the new box office blockbuster ‘Matrix Reloaded’ should not be tempted to emulate the realistic depiction of computer hacking.» Kids — don’t try this at home!
Downloading and Installing Npcap Free Edition
The free version of Npcap may be used (but not externally
redistributed) on up to 5 systems (free license details). It may also be used on unlimited
systems where it is only used
with Nmap
and/or Wireshark. Simply
run the executable installer. The full source code for each release
is available, and developers can build their apps against the SDK.
The improvements for each release are documented in
the Npcap
Changelog.
- Npcap 0.9997 installer for Windows 7/2008R2, 8/2012, 8.1/2012R2, 10/2016, 2019 (x86 and x64).
- Npcap SDK 1.05 (ZIP).
- Npcap 0.9997 debug symbols (ZIP).
- Npcap 0.9997 source code (ZIP).
The latest development source is in our
Github source repository.
Windows XP and earlier are not supported; you can use
WinPcap for these versions.
Microsoft Windows binaries
Please read
the Windows section of the
Install Guide for limitations and installation instructions for the
Windows version of Nmap. You can choose
from a self-installer (includes dependencies and also the Zenmap GUI)
or the much smaller command-line zip file version. We support Nmap on Windows 7 and newer, as well as Windows Server 2008 and newer. We also maintain a guide for users
who must run Nmap on earlier Windows releases..
Note: The version of Npcap included in our installers may not always be the latest version. If you experience problems or just want the latest and greatest version, download and install
The Nmap executable Windows installer can handle Npcap
installation, registry performance tweaks, and decompressing the
executables and data files into your preferred location. It also includes the Zenmap graphical frontend. Skip all the
complexity of the Windows zip files with a self-installer:
Latest stable release self-installer: nmap-7.80-setup.exe
Latest Npcap release self-installer: npcap-0.9997.exe
We have written . Please notify us
if you encounter any problems or have suggestions for the
installer.
For those who prefer the command-line zip files (Installation Instructions; ), they are still available. The Zenmap graphical
interface is not included with these, so you need to run
nmap.exe from a DOS/command window. Or
you can download and install a superior command shell such as those
included with the free Cygwin system.
Also, you need to run the Npcap
and Microsoft Visual C++ 2013 Redistributable Package
installers which are included in
the zip file. The main advantage is that these zip files are a fraction of
the size of the executable installer:
Latest stable command-line zipfile: nmap-7.80-win32.zip
Install Nmap
Part of securing a network involves doing vulnerability testing. This means trying to infiltrate your network and discover weaknesses in the same way that an attacker might.
Out of all of the available tools for this, is perhaps the most common and powerful.
You can install nmap on an Ubuntu or Debian machine by entering:
One of the side benefits of installing this software is an improved port mapping file. You can see a much more extensive association between ports and services by looking in this file:
Besides having almost 20 thousand lines, this file also has additional fields, such as the third column, which lists the open frequency of that port as discovered during research scans on the internet.
История
Nmap был впервые опубликован в сентябре 1997 года, как статья в журнале Phrack Magazine с исходным кодом включены. С помощью и вкладами сообщества компьютерной безопасности его развитие продолжалось. Усовершенствования включали внедрение операционной системы дактилоскопии, дактилоскопического обслуживания, переписанный код (с языка C на C++), дополнительные виды сканирования, поддержка протокола (например, IPv6, протокол SCTP) и новые программы, которые дополняют основные функции cканирования. Изменения включали в себя:
- 12 декабря 1998—Выпущена Nmap 2.00, включая операционную систему сканирования отпечатков пальцев
- 11 апреля 1999—NmapFE, передняя часть GTK+, в комплекте с Nmap
- 7 декабря 2000—порт Windows
- 28 августа 2002—переписка с языка С на C++ (язык программирования)
- 16 сентября 2003—первый публичный выпуск, включающий обнаружение служебной версии
- 31 августа 2004—ядро сканирования переписано для версии 3.70, новый движок называется ultra_scan
Лето 2005-Nmap выбран для участия в Google Summer of Code. Добавлены возможности Zenmap, который использует скриптовый движок (НСЕ), Netcat, и операционная система 2-го поколения.
- 13 декабря 2007—был выпущен Nmap 4.50, 10-летие издания. Включены Zenmap, операционная система 2-го поколения, и nmap, использующий скриптовый движок.
- 30 марта 2009 года—аварийный релиз Nmap 4.85BETA5, использование Nmap Scripting Engine (NSE) для выявления вирусные инфекции
- 16 2009—5 июля.00 в комплекте с netcat-замена и Ndiff сканирования сравнение инструментов.
- 28 января 2011—5.50 включена генерация Netcat пакетов Nping
- 21 мая 2012—6.00 выпущен с полной поддержкой IPv6.
- 9 ноября 2015—Nmap 7.00
- 20 декабря 2016—Nmap 7.
«Changelog» nmap фиксирует все изменения.
3rd Party Docs
Some of the best (and certainly most creative!) documentation has been contributed by Nmap users themselves. If you write an interesting or useful document about Nmap, please send the announcement to nmap-dev or directly to Fyodor.
James “Professor” Messer has released Nmap Secrets, the first interactive video training course for Nmap. It contains 11 modules with hours of instruction starting with “Nmap Basics” and proceeding up to firewall evasion and “Ninja Scanning”. The course costs $197 and offers a money-back guarantee. James also runs regular free Nmap Webinars. Learn more at ProfessorMesser.Com.
A detailed Nmap Tutorial has been maintained since 2003 by Andrew Bennieston (Stormhawk).
Mohamed Aly has created this single-page (PDF) Nmap Mindmap as a convenient reference to all of the major Nmap options.
Mark Wolfgang has written an excellent paper on advanced host
discovery using Nmap. Here is the PDF paper and associated source
code.
Adrian Crenshaw has made a couple excellent video tutorials
in Flash. Check out Volume 1: Basic
Nmap Usage and Volume 2: Port
Scan Boogaloo.
Long-time Nmap contributor Lamont Granquist wrote a clear and useful (if dated) guide to getting started
with nmap.
Raven Alder has written a short guide named Nmap — looking from the outside in for LinuxChix.
Uh-oh! Security expert and Counter Hack author Ed Skoudis
has discovered our secret
partnership with Microsoft!
The Girl with the Dragon Tattoo
The Girl with the Dragon Tattoo (Swedish: Män som hatar kvinnor) is a 2009 Swedish thriller film (Wikipedia,
IMDB, Amazon) based on the Internationally bestselling novel by Stieg Larsson. It follows Lisbeth, a troubled young hacker suffering from Asperger syndrome and a history of abuse by authority figures, as she works with a journalist trying to solve a 40-year old murder mystery. It was the third-highest grossing non-English film of 2009.
The Nmap scene lasts only moments and occurs about 6 minutes in. Note that this is the original film (English subtitled version available on Amazon). A big-budget Hollywood remake was released in 2011 (IMDB, Wikipedia, Amazon), though they may have ruined it by cutting the Nmap scene!.
Trailer for the 2010 US/UK subtitled release:
Определяем имя и версию ОС
Наверное, это одна из самых известных функций Nmap. Отправляя машине нестандартные пакеты и сопоставляя ее ответ (время ответа, значения полей TTL, MTU, ACK и многое другое) с «базой отпечатков ОС» (), Nmap способен достаточно точно определить запущенную на машине ОС. Все, что нужно сделать, — это запустить Nmap с флагом :
Однако далеко не всегда Nmap способен на 100% правильно угадать ОС. Если сделать это не получится, Nmap выведет на экран наиболее близкие к правильному варианты, заботливо снабдив их «процентом попадания»: 90%, 82%…
Более того, ты можешь пойти еще дальше и воспользоваться флагом , чтобы заставить Nmap попытаться определить версию ОС, версию служб и даже провести более детальный анализ служб с помощью скриптов NSE (о них позже):
Предположения Nmap о версии ОС сканируемой машины
Broken Saints
Broken Saints (Wikipedia, IMDB, Amazon) is an award-winning animated film series (motion comic) produced in 24 chapters first published online between 2001 and 2003. It was then improved for the 2006 DVD release distributed by 20th Century Fox. It is a complex, 12-hour tale of four strangers from «the quiet corners of the globe» connected by a vision they all receive of coming evil.
One of those four strangers, Raimi, is a young security software developer who uses Nmap to compromise systems and uncover corporate treachery at his estranged employer. The Nmap Scene is in Chapter 2, Cryptic, and can be . You don’t really need to watch Chapter 1 first, but it is . The Nmap cameo was first discovered by David Alexander. Screenshots:
 |
 |
 |
 |
Nmap Book
|
Nmap Network Scanning is the official guide to Nmap. From explaining port scanning basics for novices to detailing low-level packet crafting methods used by advanced hackers, this book by Nmap’s original author suits all levels of security and networking professionals. The reference guide documents every Nmap feature and option, while the remainder demonstrates how to apply them to quickly solve real-world tasks. Examples and diagrams show actual communication on the wire. Topics include subverting firewalls and intrusion detection systems, optimizing Nmap performance, and automating common networking tasks with the Nmap Scripting Engine. More than half of the book is available free online. It was written in English but . |
Nmap Network Scanning
| Nmap参考指南(Man Page) | ||
|---|---|---|
Nmap参考指南(Man Page)
目录
- 译注
- 选项概要
- 目标说明
- 主机发现
- 端口扫描基础
- 端口扫描技术
- 端口说明和扫描顺序
- 服务和版本探测
- 操作系统探测
- 时间和性能
- 防火墙/IDS躲避和哄骗
- 输出
- 其它选项
- 运行时的交互
- 实例
- Bugs
- 作者
- 法律事项(版权、许可证、担保(缺)、出口限制)
描述
| 注意 | |
|---|---|
|
本文档描述了Nmap版本4.50。最新文档以英语 |
Nmap (“Network Mapper(网络映射器)”) 是一款开放源代码的
网络探测和安全审核的工具。它的设计目标是快速地扫描大型网络,当然用它扫描单个
主机也没有问题。Nmap以新颖的方式使用原始IP报文来发现网络上有哪些主机,那些
主机提供什么服务(应用程序名和版本),那些服务运行在什么操作系统(包括版本信息),
它们使用什么类型的报文过滤器/防火墙,以及一堆其它功能。虽然Nmap通常用于安全审核,
许多系统管理员和网络管理员也用它来做一些日常的工作,比如查看整个网络的信息,
管理服务升级计划,以及监视主机和服务的运行。
Nmap输出的是扫描目标的列表,以及每个目标的补充信息,至于是哪些信息则依赖于所使用的选项。
“所感兴趣的端口表格”是其中的关键。那张表列出端口号,协议,服务名称和状态。状态可能是
(开放的),(被过滤的),
(关闭的),或者(未被过滤的)。
Open(开放的)意味着目标机器上的应用程序正在该端口监听连接/报文。
(被过滤的) 意味着防火墙,过滤器或者其它网络障碍阻止了该端口被访问,Nmap无法得知
它是
(开放的) 还是 (关闭的)。
(关闭的) 端口没有应用程序在它上面监听,但是他们随时可能开放。
当端口对Nmap的探测做出响应,但是Nmap无法确定它们是关闭还是开放时,这些端口就被认为是
(未被过滤的)
如果Nmap报告状态组合
和
时,那说明Nmap无法确定该端口处于两个状态中的哪一个状态。
当要求进行版本探测时,端口表也可以包含软件的版本信息。当要求进行IP协议扫描时
(),Nmap提供关于所支持的IP协议而不是正在监听的端口的信息。
除了所感兴趣的端口表,Nmap还能提供关于目标机的进一步信息,包括反向域名,操作系统猜测,设备类型,和MAC地址。
一个典型的Nmap扫描如所示。在这个例子中,唯一的选项是,
用来进行操作系统及其版本的探测, 可以加快执行速度,接着是两个目标主机名。
例 1. 一个典型的Nmap扫描
# nmap -A -T4 scanme.nmap.org playground Starting nmap ( https://nmap.org/ ) Interesting ports on scanme.nmap.org (205.217.153.62): (The 1663 ports scanned but not shown below are in state: filtered) port STATE SERVICE VERSION 22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99) 53/tcp open domain 70/tcp closed gopher 80/tcp open http Apache httpd 2.0.52 ((Fedora)) 113/tcp closed auth Device type: general purpose Running: Linux 2.4.X|2.5.X|2.6.X OS details: Linux 2.4.7 - 2.6.11,Linux 2.6.0 - 2.6.11 Uptime 33。908 days (since Thu Jul 21 03:38:03 2005) Interesting ports on playground。nmap。或者g (192.168.0.40): (The 1659 ports scanned but not shown below are in state: closed) port STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn 389/tcp open ldap? 445/tcp open microsoft-ds Microsoft Windows XP microsoft-ds 1002/tcp open windows-icfw? 1025/tcp open msrpc Microsoft Windows RPC 1720/tcp open H.323/Q.931 CompTek AquaGateKeeper 5800/tcp open vnc-http RealVNC 4.0 (Resolution 400x250; VNC TCP port: 5900) 5900/tcp open vnc VNC (protocol 3.8) MAC Address: 00:A0:CC:63:85:4B (Lite-on Communications) Device type: general purpose Running: Microsoft Windows NT/2K/XP OS details: Microsoft Windows XP Pro RC1+ through final release Service Info: OSs: Windows,Windows XP Nmap finished: 2 IP addresses (2 hosts up) scanned in 88.392 seconds
Базовые возможности
Перед тем как перейти к обсуждению продвинутых возможностей Nmap, давай уделим немного внимания использованию Nmap на базовом уровне. Ты можешь возразить, что говорить тут не о чем, — достаточно всего лишь натравить Nmap на нужный хост, и спустя некоторое время он выдаст на экран информацию об открытых портах:
Это действительно так, но стоит иметь в виду две особенности реализации Nmap. Первая: запущенный с правами обычного пользователя Nmap крайне неэффективен. Весь процесс сканирования при этом фактически сводится к попытке установить полноценное соединение с каждым из портов. В случае протокола TCP это значит, что Nmap пошлет на удаленную сторону пакет SYN; если запрошенный порт открыт, машина ответит пакетом SYN/ACK, после чего Nmap отправит пакет ACK и только потом закроет соединение с помощью пакета FIN.
Весь этот процесс осуществляется с помощью системного вызова connect() и, по сути, целиком ложится на сетевой стек ОС. В результате страдает как производительность сканирования, так и скрытность (сервисы, висящие на сканируемых портах, будут активно логировать соединения).
Совсем по-другому Nmap ведет себя, когда запущен с правами root:
В этом случае он полностью берет на себя формирование пакетов и управление соединением. Подключение к открытым портам будет выглядеть так: Nmap посылает SYN, машина отвечает SYN/ACK, Nmap посылает FIN, разрывая наполовину открытое соединение (это называется TCP SYN сканирование). В результате сервис, висящий на порте, не логирует попытку соединения, а Nmap способен обнаружить брандмауэр, который просто отбрасывает SYN-пакеты вместо того, чтобы отправить в ответ SYN/ACK (порт открыт) или FIN (порт закрыт), как это должна делать операционная система по умолчанию. Кроме того, этот способ сканирования намного более производительный.
Вторая особенность Nmap заключается в том, что на самом деле он сканирует не весь диапазон портов (65 536), а только 1000 портов типовых служб, определенных в файле . Так что, если кто-то повесит сервис на нестандартный порт, которого просто нет в этом файле, Nmap его не увидит. Изменить подобное поведение можно при помощи такой команды:
Nmap будет использовать сканирование типа TCP SYN и UDP-сканирование для всего диапазона портов.
Linux RPM Source and Binaries
Many popular Linux distributions (Redhat, Mandrake, Suse, etc) use
the RPM package management system for
quick and easy binary package installation. We have
written a detailed , though these simple commands usually do
the trick:
rpm -vhU https://nmap.org/dist/nmap-7.80-1.x86_64.rpm rpm -vhU https://nmap.org/dist/zenmap-7.80-1.noarch.rpm rpm -vhU https://nmap.org/dist/ncat-7.80-1.x86_64.rpm rpm -vhU https://nmap.org/dist/nping-0.7.80-1.x86_64.rpm
Latest stable release:x86-64 (64-bit Linux) Nmap RPM: nmap-7.80-1.x86_64.rpmx86-64 (64-bit Linux) Ncat RPM: ncat-7.80-1.x86_64.rpmx86-64 (64-bit Linux) Nping RPM: nping-0.7.80-1.x86_64.rpm
Optional Zenmap GUI (all platforms): zenmap-7.80-1.noarch.rpm
Source RPM (includes Nmap, Zenmap, Ncat, and Nping): nmap-7.80-1.src.rpm