Неткат — netcut последняя версия 3.0.119
Содержание:
- HTTP Requests with Netcat Commands
- Сравнение альтернативных программ:
- Пользователи, которые скачивали неткат — netcut, также скачивали:
- Ports and reimplementations
- How to connect via SSL (HTTPS) to Ncat
- How to make a web server with Ncat
- Ncat Options
- Особенности движков
- Описание редакции
- Простой в использовании инструмент управления сетью
- Emulation of diagnostic services
- Launching Reverse (Backdoor) Shells
- Netcat Versions
- Netcat the Multi-purpose Networking Tool
HTTP Requests with Netcat Commands
We’ve covered how you can use Netcat to host HTML pages on your local system. But the utility program can also be used to make web requests to outside servers. In this way, Netcat will essentially function as a web browser by obtaining raw HTML code.
Along with a tool like Varonis Edge, Netcat can be helpful for IT professionals who are looking into internet traffic issues or proxies. Here’s an example of how to obtain the HTML content from Google’s homepage:
printf “GET / HTTP/1.0\r\n\r\n” | nc google.com 80
Note that the port number 80 is required for this type of command since the world wide web uses it as a default for TCP over IP connections.
Сравнение альтернативных программ:
|
Arcai.com’s netcut-defender |
Bello Network Monitoring WinGUI |
Bytemon Network Monitor |
BWMeter |
|
| Описание | Скачать Arcai.com’s netcut-defender, версия 2.1.5 | Для недорогого и эффективного мониторинга сетей и серверов | Скачать Bytemon Network Monitor, версия 2.1.3.1 | Скачать BWMeter, версия 8.4.8 |
| Рейтингу | ||||
| Загрузки | 463 | 61 | 13 | 25 |
| Цена | $ 0 | $ 0 | $ 79 | $ 30 |
| Размер файла | 1.69 MB | 1.26 MB | 6.80 MB | 1.60 MB |
|
Download |
Download |
Download |
Download |
Пользователи, которые скачивали неткат — netcut, также скачивали:
Мы рады посоветовать вам программы которые понравились другим пользователям неткат — netcut. Вот список программ, аналогичных неткат — netcut:
Camera Card Recovery Software
3.0.1.5
Восстановите поврежденные и утерянные фото и видео
скачать
Резервирование и восстановление
Рейтинг пользователей
Camera Card Recovery
3.0.1.5
Восстановите удаленные фотографии с вашего цифрового фотоаппарата
скачать
Резервирование и восстановление
Рейтинг пользователей
Repair NTFS File System
4.0.1.6
Восстановите файлы, которые вы считали утерянными.
скачать
Резервирование и восстановление
Рейтинг пользователей
Recover iPod Missing Files
4.0.1.6
Восстанавливайте удаленные файлы с вашего iPod
скачать
Резервирование и восстановление
Рейтинг пользователей
Ports and reimplementations
The original version of netcat was a Unix program. The last version (1.10) was released in March 1996.
There are several implementations on POSIX systems, including rewrites from scratch like GNU netcat or OpenBSD netcat, the latter of which supports IPv6 and TLS. The OpenBSD version has been ported to the FreeBSD base and Windows/Cygwin.Mac OS X comes with netcat installed as of OSX 10.13 or users can use MacPorts to install a variant.
A DOS version of netcat called NTOOL is included in the FreeDOS Package group Networking. It is based on the WatTCP stack and licensed under the European Union Public Licence Version 1.1.
Known ports for embedded systems includes versions for Windows CE (named «Netcat 4 wince») or for the iPhone.
BusyBox includes by default a lightweight version of netcat.
Solaris 11 includes netcat implementation based on OpenBSD netcat.
Socat is a more complex variant of netcat. It is larger and more flexible and has more options that must be configured for a given task. On February 1, 2016, Santiago Zanella-Beguelin and Microsoft Vulnerability Research issued a security advisory regarding a composite Diffie-Hellman parameter which had been hard-coded into the OpenSSL implementation of socat. The implausibility that a composite might have been unintentionally introduced where a prime number is required has led to the suspicion of sabotage to introduce a backdoor software vulnerability. This socat bug affected version 1.7.3.0 and 2.0.0-b8 it was corrected in following releases from 1.7.3.1 and 2.0.0-b9.
Cryptcat is a version of netcat with integrated transport encryption capabilities.
In the middle of 2005, Nmap announced another netcat incarnation called Ncat. It features new possibilities such as «Connection Brokering», TCP/UDP Redirection, SOCKS4 client and server support, ability to «Chain» Ncat processes, HTTP CONNECT proxying (and proxy chaining), SSL connect/listen support and IP address/connection filtering. Like Nmap, Ncat is cross-platform.
On some systems, modified versions or similar netcat utilities go by the command name(s) , , , , , , .
How to connect via SSL (HTTPS) to Ncat
How can we see that in the first, in the second case, the response code 302 Moved Temporarily is returned to us – that is, we are redirected to another page:
HTTP/1.1 302 Moved Temporarily Server: nginx Content-Type: text/html; charset=utf-8 Connection: close Location: https://hackware.ru/any_page.php Date: Tue, 07 May 2019 02:56:40 GMT X-Page-Speed: 1.13.35.2-0 Cache-Control: max-age=0, no-cache
As can be understood from the Location directive, we are redirected to the HTTPS protocol.
To connect to Ncat via SSL we need to:
- specify option —ssl
- specify the appropriate port number
For the HTTPS protocol, the default port is 443, so we connect as follows:
ncat -C --ssl hackware.ru 443
Then:
GET / HTTP/1.0 Host: hackware.ru
As a result, the HTML code of the requested page is finally shown to us:

How to make a web server with Ncat
In fact, it will be a single file web server, but, nevertheless, it is still an interesting feature.
So, create a file hello.http and add the following content to it:
HTTP/1.0 200 OK
<html>
<body>
<h1>Hello, world!</h1>
</body>
</html>
Run Ncat on the server:
ncat -l 43210 < hello.http
In the web browser, open the address of the remote host with the port: http://185.26.122.50:43210
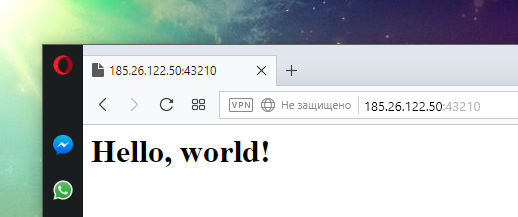
By the way, ncat on the server will show which headers were sent by the web browser:

Another example from the official manual on ncat:
nc -lk -p 8080 --sh-exec "echo -e 'HTTP/1.1 200 OK\r\n'; cat index.html"
Or, if you are a Windows user:
ncat -lk -p 8080 --sh-exec "echo HTTP/1.1 200 OK& echo(&type index.html"
These commands will start the HTTP server that makes the index.html file from the current working directory accessible. To open this file you need to visit the browser page http://localhost:8080/. If instead of -p 8080 you specify -p 80, then from the URL you can delete :8080. Please note that this file will be sent regardless of the requested URL – to change the file that is sent, you need to change the Ncat command or use the httpd.lua script.
Ncat Options
Usage:
ncat
Options:
Options taking a time assume seconds. Append 'ms' for milliseconds,
's' for seconds, 'm' for minutes, or 'h' for hours (e.g. 500ms).
-4 Use IPv4 only
-6 Use IPv6 only
-U, --unixsock Use Unix domain sockets only
-C, --crlf Use CRLF for EOL sequence
-c, --sh-exec <command> Executes the given command via /bin/sh
-e, --exec <command> Executes the given command
--lua-exec <filename> Executes the given Lua script
-g hop1 Loose source routing hop points (8 max)
-G <n> Loose source routing hop pointer (4, 8, 12, ...)
-m, --max-conns <n> Maximum <n> simultaneous connections
-h, --help Display this help screen
-d, --delay <time> Wait between read/writes
-o, --output <filename> Dump session data to a file
-x, --hex-dump <filename> Dump session data as hex to a file
-i, --idle-timeout <time> Idle read/write timeout
-p, --source-port port Specify source port to use
-s, --source addr Specify source address to use (doesn't affect -l)
-l, --listen Bind and listen for incoming connections
-k, --keep-open Accept multiple connections in listen mode
-n, --nodns Do not resolve hostnames via DNS
-t, --telnet Answer Telnet negotiations
-u, --udp Use UDP instead of default TCP
--sctp Use SCTP instead of default TCP
-v, --verbose Set verbosity level (can be used several times)
-w, --wait <time> Connect timeout
-z Zero-I/O mode, report connection status only
--append-output Append rather than clobber specified output files
--send-only Only send data, ignoring received; quit on EOF
--recv-only Only receive data, never send anything
--allow Allow only given hosts to connect to Ncat
--allowfile A file of hosts allowed to connect to Ncat
--deny Deny given hosts from connecting to Ncat
--denyfile A file of hosts denied from connecting to Ncat
--broker Enable Ncat's connection brokering mode
--chat Start a simple Ncat chat server
--proxy <addr> Specify address of host to proxy through
--proxy-type <type> Specify proxy type ("http" or "socks4" or "socks5")
--proxy-auth <auth> Authenticate with HTTP or SOCKS proxy server
--ssl Connect or listen with SSL
--ssl-cert Specify SSL certificate file (PEM) for listening
--ssl-key Specify SSL private key (PEM) for listening
--ssl-verify Verify trust and domain name of certificates
--ssl-trustfile PEM file containing trusted SSL certificates
--ssl-ciphers Cipherlist containing SSL ciphers to use
--ssl-alpn ALPN protocol list to use.
--version Display Ncat's version information and exit
See the ncat(1) manpage for full options, descriptions and usage examples
Особенности движков
Конкуренты достойны друг друга и могут похвастаться индивидуальными особенностями. Движок ЮМИ стал доступен широкой аудитории в 2007 году. Это универсальная система управления контентом от российских разработчиков. Она активно развивается с момента создания и стремительно завоевывает награды в различных категориях. В настоящее время насчитывается более миллиона пользователей данной платформы. Учитывая, что продукт распространяется только в России и СНГ, количество скачиваний свидетельствует о высокой популярности.
Платформа NetCat разрабатывалась начиная с 1999 года. Она представляет собой многофункциональный продукт и доступна в нескольких вариациях. Множество веб-студий используют ее для создания сайтов своим клиентам. Расширение базовых возможностей осуществляется на модульной основе.
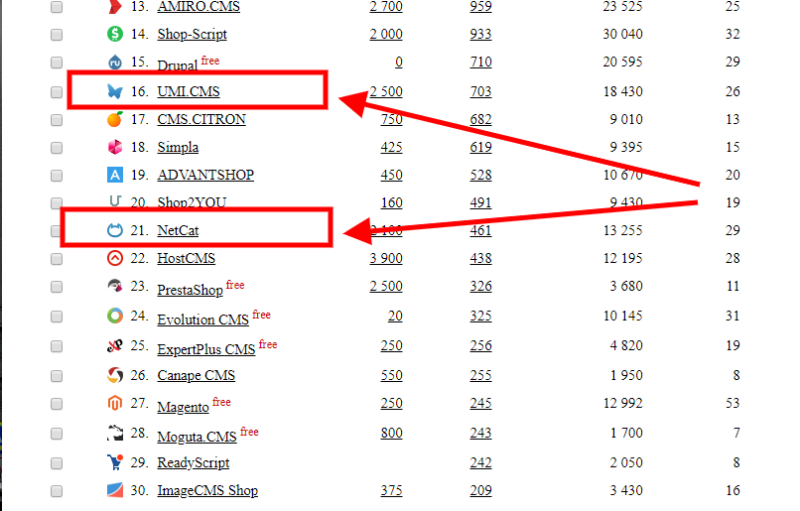
Представленные движки написаны на языке программирования PHP. Для хранения информации используются базы данных MySQL. Оба продукта имеют открытый исходный код, но при этом регламентируют порядок внесения изменения. На сайте UMI расположен подробный список изменений, которые можно осуществлять без специального разрешения разработчиков. Перечень включает в себя несколько десятков позиций. Это позволяет программистам произвести тонкие настройки, корректируя системный скрипт.
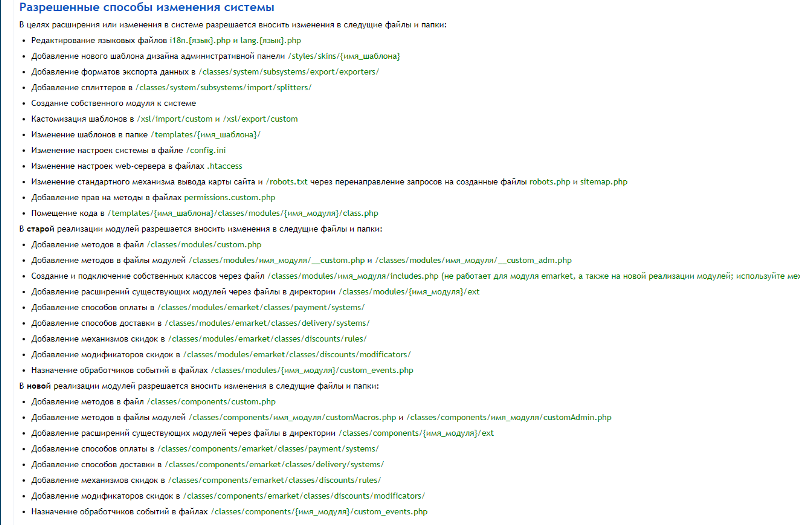
Политика Неткэт несколько иная. Пользователи имеют очень строгие ограничения, которые запрещают копировать софт и вносить в него изменения. Это означает, что придется пользоваться тем, что предоставляют создатели. В противном случае, действия будут расценены как нарушение авторских прав. В этом вопросе UMI выглядит более лояльно и привлекательно.
Еще одним отличием является частота обновлений. Оба продукта активно поддерживаются создателями, но обновления для UMI выходят в несколько раз чаще, чем для NetCat. В новых версиях совершенствуется функционал, повышается степень защиты, устраняются ошибки, улучшается быстродействие и так далее. Регулярный апгрейд можно считать жирным плюсом и UMI в этом вопросе превосходит конкурента.
Описание редакции
Простой в использовании инструмент управления сетью
Netcut — программное обеспечение для управления сетью. С помощью этой программы сетевой администратор может воспользоваться таблицей IP-MAC адресов для защиты сети от ложных ARP и других форм атак и использования уязвимостей. Netcut отображает данные, включающие статус, IP адрес подключения, имя хоста и физический адрес. Программа позволяет в реальном времени отслеживать подключение и отключение устройств в сети без необходимости постоянно обновлять окно. Кроме того, администратор может отключить сеть, включить ее, контролировать работу любого устройства, в частности роутеров, компьютеров, ноутбуков, смартфонов, планшетов и игровых приставок. Приложение может быть использовано для изменения MAC-адреса или его копирования. Netcut включает Nectcut Defender, защитное ПО для сервера. Программу очень просто установить, настроить и использовать, она подходит для выполнения множества задач и не требует глубоких знаний в области сетевого администрирования. Netcut использует очень малую часть системных ресурсов. Приложение также предлагает доступ к большому количеству онлайн-ресурсов, подсказок и экспертных советов, что помогает новичкам полностью раскрыть его потенциал. Netcut может работать с разными типами сетей, включая школьные, рабочие локальные сети и сети Wi-Fi. Программу можно скачать совершенно бесплатно, она совместима с большинством версий MS Windows.
скачать
Emulation of diagnostic services
Since Ncat can act as a server that accepts anything and displays it on the screen (or saves it to a file), you can run Ncat in listening mode, and in a program whose network activity interests us, we can specify the address of Ncat. As a result, the program will contact Ncat, and in turn, Ncat will show us everything that this program sent to it.
Suppose I’m wondering what kind of request the dig command sends — this command is used to convert host names to IP addresses and back. I know that by default it uses UDP port 53. Therefore, on my computer, I run ncat with the -l option (enables listening), with the -u option (meaning using UDP) and specifying port 53:
sudo ncat -l -u 53
On the same computer in another console, I make a request where, as a server, to which the program should access, I specify localhost:
dig hackware.ru @localhost

As it turned out, dig does not use plain text, but binary data, so unreadable characters were displayed in the ncat console. Although even so it is clear that the domain is transmitted in plain text (almost) and 3 attempts are made. By the way, Ncat has options for saving binary data. That is, if you wish, you can save them correctly and then analyze them with a hexadecimal editor.
Launching Reverse (Backdoor) Shells
To get started, you need to enable the shell tool over a Netcat command by using Netcat reverse shell:
nc -n -v -l -p 5555 -e /bin/bash
Then from any other system on the network, you can test how to run commands on host after successful Netcat connection in bash.
nc -nv 127.0.0.1 5555
A reverse shell is a remote access approach where you run administrative commands from one terminal while connecting to another server on the network. To get started, you need to enable the shell tool over a Netcat command by using Netcat reverse shell:
nc -n -v -l -p 5555 -e /bin/bash
Then from any other system on the network, you can test how to run commands on the selected host after successful Netcat connection in bash:
nc -nv 127.0.0.1 5555
Netcat Versions
It happened that Netcat has many versions written by different authors. The original version was called netcat (nc). She quickly became popular, but at some point the author stopped developing it and, despite its popularity, no one else supported either. For this reason, the program was rewritten several times by different authors, and sometimes completely from scratch.
netcat (nc)
This is the original program, the latest release of which was in January 2007. Its version is 1.10.
On some systems, like Kali Linux, this version is called nc.traditional:
nc.traditional -h
Displays help for this program and shows the version
ncat
This is a modern version of netcat, which is written from scratch, without using the original netcat code. The authors of ncat are the authors of the famous Nmap program.
Ncat repeats almost all the functionality of the original program and contains additional features.
Ncat became the official replacement for the original netcat in some Linux distributions, for example, in Red Hat Enterprise Linux, CentOS, which are often used as web servers. For this reason, you will find Ncat on many computers on the network — for example, Ncat is installed on my shared hosting instead of Netcat.
Ncat provided in the Nmap package and, therefore, is available for different platforms, including Windows. That is, to install Ncat on Windows, it is enough to install NMap.
In Kali Linux, Ncat is for some reason contained in packages for the i386 architecture and is not contained in the NMap package, so the installation is as follows:
sudo dpkg --add-architecture i386 && sudo apt update sudo apt install ncat
In Arch Linux, BlackArch and their derivatives, it is enough to install NMap to install Ncat:
sudo pacman -S nmap
dbd
Another Netcat clone, created to be portable and offers strong encryption. It works on Unix-like operating systems and on Microsoft Win32.
sbd
And another Netcat clone, portable, offers strong encryption, among the features: AES-128-CBC + HMAC-SHA1 encryption, program execution (-e), source port selection, continuous reconnection with delay and other features.
Or as stated in another description: a secure backdoor for Linux and Windows.
webhandler
PHP system functions handler, as well as an alternative netcat handler.
Other variants of this classic tool include the amazingly versatile Socat, OpenBSD nc, Cryptcat, Netcat6, pnetcat, SBD, and the so-called GNU Netcat.
On some systems, modified versions or similar netcat utilities use the command names: nc, ncat, pnetcat, socat, sock, socket, sbd.
So, for your work, you can choose one of these versions, which one you like best. When searching for interesting programs on other people’s machines, do not forget about alternatives if the netcat itself is not there.
In this manual, I will consider mainly ncat.
Netcat the Multi-purpose Networking Tool
Linux netcat — nc command examples
netcat — nc — Utility
The netcat utility or nc is often referred to as the Swiss Army Knife for working with TCP/IP networks. This tool is very popular amongst System Administrators and Network Administrators because of its wide range of capabilities. The netcat utility is used for almost anything under the sun involving TCP, UDP, or UNIX-domain sockets. Netcat can open TCP connections, send UDP packets of data, listen on arbitrary TCP and UDP ports, carry out port scanning, transfer data from one server to another. In the following examples I will be using an Ubuntu 14.04 LTS system and a CentOS 6.5 system.
Installing netcat on Ubuntu
If you need to install netcat, you can use the following commands:
Note: In Ubuntu 14.04 LTS netcat came pre installed. (No need to install)
Checking for an Open Port
In this example we will use netcat to interrogate a port to see if it is open. We will use the netcat command in conjunction with the «-v» and «-n» flags. The «-v» flag specifies that we would like verbose output (more detailed). The «-n» option specifies that we do not wish to use DNS or service lookups on any addresses, hostnames or ports.
Example Command: nc -vn 192.168.0.17 22
In the above example we have specified the IP address of a RHEL (Red Hat Enterprise Linux 6.3) server followed by the port we wish to interrogate. In this example we are looking at port 22 (normally used for ssh).
As we can see from the output port 22 is open for connections. If we now check for a port which is closed, you will see the difference in the output from the command:
netcat as a Port Scanner
Another popular use of the netcat command is to use it as a port scanner. In this example we will be using the flags «-w» and «-z» in addition to the «-v» and «-n» flags. The «-w» flag is used to specify a timeout limit. By default, netcat will listen forever, however, in this example we are going to use a more realistic value of «1» second. The «-z» flag specifies that netcat should merely scan for listening daemons without sending any data. We will also specify a range of ports to check. In this example we are only going to check ports 1 through to 30.
Example Command: nc -vnz -w 1 192.168.0.17 1-30
We can clearly see from the above output that a connection to port 22 has succeeded.
You can also specify more than one port to scan.
Example Command: nc -vnz -w 1 192.168.0.17 20 21 22 23 24 25
In the above example, we are going to scan ports «20, 21, 22, 23, 24 and 25».
Port Scanning UDP ports
In this example we are going to specify «UDP» ports to be scanned. To specify UDP we will use the «-u» flag. In the example below we are going to scan ports «60 through to 80».
Example Command:nc -vnzu -w 1 192.168.0.17 60-80
Having a Chat with Netcat
In this example we will use an Ubuntu 14.04 LTS terminal and connect this to a remote terminal on a CentOS 6.5 Server.
On the Ubuntu system, we need to identify the IP address. This can be done by issuing the command ip a s
From the above we can see that the IP address in use on interface «eth0» is 192.168.0.11
This IP address is only needed by the CentOS server. Now, on the Ubuntu system we issue the following command:nc -lp 2468
Here we are instructing netcat to listen on port 2468.
Now on the remote CentOS server we issue the following command:nc 192.168.0.11 2468
Here we are telling our CentOS server to make a connection to our Ubuntu system on port 2468.
Now any text typed on one terminal will now appear on the other terminal screen. (Warning, this is not a secure way to chat!)Ubuntu System
Output received on CentOS system
For more information regarding netcat/nc command
As always a vast amount of information can be looked at via the man pages. To view more information regarding netcat, issue the command man nc