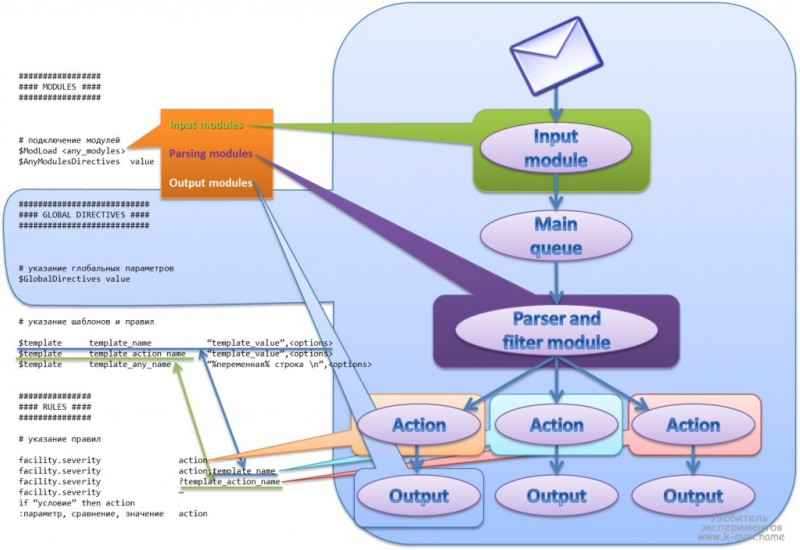
Как работает ключ mifare и как его скопировать
Содержание:
- What «getting together» means today
- Understanding following (previously called «tracking»)
- Step 2: the computer review
- Основные характеристики
- Link types
- Файловая система Keybase (KBFS)
- Attacks 1 and 2: DDOS and Corrupted Data
- Subteams, quick ‘n’ easy
- Keybase Client Integrity
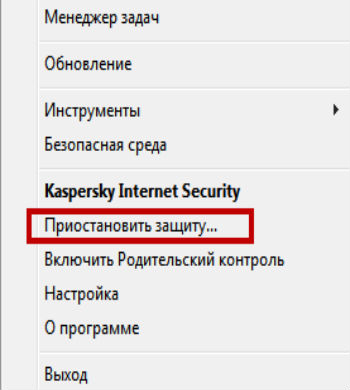
- Копирование идентификатора
- Sibkeys
- Team features
- Команды
- Decrypting & verifying
What «getting together» means today
For many weeks, everyone on earth has faced the same question: «How do we keep life moving forward if we can’t meet in person?» Teachers, small businesses, big businesses, local governments, and even our families: they’ve all turned to video communications. The world’s connections are
unbroken thanks to screens and cameras, and Zoom has exploded from an enterprise application to a household
name, helping to keep the economy alive and
families together.
Hundreds of millions of participants (free and paid) are using it every day. My neighbor, a
woodworking artist, carved and painted this:
by Mac Rogers
Animals are using Zoom, night and day.
Understanding following (previously called «tracking»)
We get some big questions about Keybase following:
- When should I follow?
- What does it get me?
- Is it a «web of trust?»
Hopefully this page can clarify and answer your q’s.


Therefore, any cryptographic action on Maria follows 3 basic steps:
Step 2: the computer review

To satisfy the client, the tweet must be special. It must link to a signed statement which claims to be from maria on Keybase.
In simplest terms, the Keybase client guarantees that «maria» has access to three things: (1) the Keybase account, (2) the twitter account, and (3) the private key referenced
back in step 1.
All this happens really fast in the client with no inconvenience to you. And it happens for all of maria’s identities: her twitter account, her personal website, her github account, etc.
maria2929 on : https://twitter.com/2131231232133333... pasc4l_programmer on github: https://gist.github.com/pasc4... admin of mariah20.com via HTTPS: https://mariah20/keybase.tx... Is this the maria you wanted? [y/N]
The advantages of public following
We hope this doc helps. We’ll revise it as questions/suggestions arrive in our github issue #100 (I don’t understand tracking).
footnote 1: the PGP web of trust
In the web of trust model, you know you have Maria’s key because you trust John, and John signed a statement
saying that another key belongs to his friend «Carla», and then Carla in turn signed a statement saying that Maria is someone whose driver’s license
and key fingerprint she reviewed at a party. Your trust of Maria’s key is a function of these such connections.
you → john → carla → mariayou → herkimer → carla → maria
The PGP web of trust has existed for over 20 years. However it is very difficult to use, it requires in-person verifications,
and it’s hard to know what trust level to assign transitively. (Herkimer reports that Carla was drunk; John can’t remember, but he was drunk too, and who’s Carla again???)
Основные характеристики
Изготовление ключей основывается на использовании главных критериев моделей бесконтактных карт ISO 14443. Этот стандарт позволяет использовать ключ вместе с остальными технологиями доступа.
Сейчас в банковские карты массово внедряют технологию MF-идентифицирования. Также во многих современных телефонах есть встроенная программа NFC, позволяющая осуществлять беспроводную передачу данных на небольшом радиусе.
Брелок Mifare и ключ-карты Mifare – крайне удобные устройства с возможностью бесконтактного распознавания. Они характеризуются следующими преимуществами:
- Для них не нужны отдельные источники питания, которые требовали бы постоянной замены.
- Не нужно контактировать со считывающим устройством, процесс осуществляется на расстоянии до 10 см.
- Данные ключа считываются быстрее, чем за секунду.

Разновидность брелка Mifare
Link types
Each section below starts with an example (and leaves out , , and , which were described above).
Appears at the beginning of a sigchain or after an account reset (may not have been inserted by legacy clients). The link’s signing key becomes the account’s first sibkey.
Add a new sibkey to the account. is a signature of the link by the new sibkey itself, made with the field set to , and makes sure that a user can’t claim another user’s key as their own.
Add a new encryption-only subkey to the account. We plan to use these in the future.
Update a PGP key to a new version (which may have new subkeys, revoked subkeys, new user IDs…). The section contains the same properties a section would. is expected to have changed, the other properties should be unchanged.
Remove the keys in from your account. Any previous links they’ve signed are still valid, but they can no longer sign new links and other users should no longer encrypt for them after seeing the link. Also reverse the effects of the links in — this can be used to remove, for instance, a .
Claim, “I am on the website ”. The client will look for a copy of the link and signature on the website, in an appropriate place. The server searches for the proof when the link is first posted, and caches its permalink (e.g. the tweet, on Twitter, the Gist, on GitHub) so that the client doesn’t have to rediscover it each time.
The section can also look like this, which claims that you control the given domain name (the client looks for the proof in DNS):
…or like this, which claims that you control the given website (the client looks for the proof at a known path):
(to ‘follow’ someone)
We call this «follow» around the interface now, but our old word is «track»…so that’s what you’ll see in your sig chain:
Make a snapshot of another user’s identity that your other devices trust. The section contains these properties:
- – Their user ID
- – Contains their username and identity generation. The server bumps the identity generation whenever the state of any of their proofs changes, as a hint to the client that it should recheck them all and possibly alert the user to the change.
- – Contains the KID and fingerprint (if applicable) of their eldest key.
- – An array of the KID and fingerprint of every one of their PGP keys
-
– An array of objects which represent their proofs. Many properties are copied directly from the relevant links in the followee’s sigchain, but there are some non-obvious ones:
- – The hash of the link which contains the proof
- – An integer representation of the proof’s link type, currently always ()
-
- – The section of the identity proof link
- – An integer representation of the account being proven (Twitter, GitHub, etc.)
- – An integer representation of whether the client could successfully verify the proof when making the tracking statement.
A repeat link for the same user replaces the previous one (the user may have re-followed due to a change in proofs).
(to «unfollow» someone)
Stop following a user. Your other devices will resume checking their identity proofs and presenting them to you whenever you interact with them. is the user’s UID.
Advertise a cryptocurrency address. Currently Bitcoin, Zcash and Zcash sapling addresses are supported.
Add or rotate a Per-user signing and encryption key.
is the signature over the sigchain link with new per-user signing key itself.
The number starts at one and increments whenever the per-user keys are rotated, typically
after a device revocation.
footnote 1: PGP key servers and lying by omission
When someone changes a PGP key — to update its expiration date or add a signature, for example — they’re expected to broadcast the change to a key server. That key server is responsible for forwarding the change to other key servers, and so on. Eventually, someone else can ask any other key server if there have been updates to the key, and receive them.
Notably, nothing stops someone from making a change to their PGP key on one computer, a different change on another computer, and sending each change to a different key server. The key servers are expected to share updates and offer their own combined versions of the key for download.
The design of PGP keys stops an attacker from creating fake updates, but a dishonest key server can still choose to ignore updates that revoke keys, revoke signatures, and add expiration dates, but publish updates that add new keys, add new signatures, and take away expiration dates.
Keybase sigchains aim to avoid this.
Файловая система Keybase (KBFS)
Keybase позволяет пользователям хранить до 250 ГБ данных в облачном хранилище под названием «файловая система Keybase». Файловая система делится на три части: общедоступные файлы, личные файлы и командные файлы. На Unix-подобных машинах файловая система монтируется в , а в Windows обычно монтируется на диск . В настоящее время мобильные версии клиента Keybase поддерживает только просмотр и скачивание файлов.
Частные файлы
Частные файлы хранятся в папке и доступны только пользователю. Частные папки также могут иметь нескольких владельцев. В отличие от публичных файлов, частные файлы зашифровываются и подписываются перед загрузкой с помощью сквозного шифрования.
Attacks 1 and 2: DDOS and Corrupted Data
We mentioned three attacks on this system. Consider the first two, which aim
to prevent honest clients from retrieving signature data for honest users. A
blunt attacker might DDoS Keybase’s servers, preventing anyone from accessing
Keybase’s data. A more sophisticated attacker might root keybase’s server,
compromise its signing keys, and start sending back corrupted data to honest
clients.
Two mechanisms, enforced by clients and third-party observers, defend against
both attacks:
- All user signature chains must grow monotonically, and can never be «rolled back»
- Whenever a user posts an addition to a signature chain, the site must
sign and advertise a change in global site state, and these updates are totally
ordered.
Untrusted Mirrors
The first implication of these requirements is that untrusted third parties
can mirror the site state, and clients can access data from either the Keybase
server or the mirrors. By requirement (2), the server must publish and sign
all site updates. A client doesn’t care where these updates come from, as long
as the signature verifies, and the site state jibes with the signature.
(We’re not aware of third-party mirrors yet, and our reference client
would need some modifications to handle a read-only server. However, we
encourage all to scrape our APIs in preparation.)
Be Honest or Get Caught
The second implication of these requirements is that a compromised server
has a choice of acting like an honest server, or making «mistakes» that
honest users can detect. An attacker who gains control of the server can:
- Selectively rollback a user’s signature chain and/or suppress updates
- Fake a «key update», and append signatures at the end of a user’s chain
- Show different versions of the site state to different users
Since version v0.3.0, the Keybase command-line client
defends clients from these server attacks. Take the example of what happens when
I «follow» Alex. My client downloads both
of our signature chains from the server, and runs them through cryptographic verification,
checking that our hash chains are well-formed and signed. It furthermore
checks new data against cached data and complains if the server has «rolled back» either
chain. My client prevents a compromised server from changing Alex’s key
the same way it prevents Eve from impersonating Alex: it checks for corroboration
of Alex’s identity and key proofs on other services (like Twitter, GitHub and DNS).
To prevent the server from «forking» my view of the site data from Alex’s, my client checks
that all signature chains are accurately captured in the site’s global
Merkle Tree data structure.
It downloads the root
of this tree from the server, and verifies it against the site’s
public key. If the check
passes, it fetches the signed root block. My UID is , so my client follows the path
down the tree, which is block . Now, my leaf is visible, showing my signature chain
finishing off at link 42, with hash , which matches the data it fetched
earlier. My client does the same for Alex’s chain. After all checks succeed,
my client signs my chain, Alex’s chain and also Merkle root at the time
of the signature; it posts this signature as a follower statement.
A very sophisticated attacker could show my client and Alex’s client
different signed Merkle roots, but must maintain these forks permanently
and can never merge.
Users «comparing notes» out-of-band immediately expose server duplicity.
Subteams, quick ‘n’ easy
Actual companies, big and small, have another concern. Consider treehouse’s devops team, or its board of directors. These groups have things to say and share that are absolutely private, just to them. From passing around technical secrets to discussing more tender business dealings, these groups will want data that can’t be decrypted by others inside their own company.
Assuming you’re an admin of , this works:
You can invite someone into a subteam even if they’re not in the parent team. We’re already doing this at Keybase: our board of directors is inside .
Other uses: maybe or . Or . That all works.
Team sigchain control is inherited. An admin of has keys for any subteams and can always add themselves.
Asking to join a team
If you know of a team, you can ask for access. Actually, I just made a team called so if you want to talk to other testers, ask for access:
As an outsider, you can’t tell who’s on a team, so Keybase will ping the admins for you. They can then add you or ignore the request.
Keybase Client Integrity
Thus, the keybase clients in the wild play a crucial role in keeping the Keybase server
honest. They check the integrity of user signature chains, and can find
evidence of malicious rollback. They alert Alice when her following of
Bob breaks, if either Bob or the server was compromised.
They check the site’s published Merkle tree root for consistency against
known signature chains. And they sign proofs when all these checks complete,
setting up known safe checkpoints to hold the server accountable to in the future.
So everything depends on the integrity of the Keybase clients, that they
are functioning properly and aren’t compromised. We offer several
safeguards to protect client integrity. First, we keep an Open API and state that
our open-source client is simply a reference client, and that developers are free
to make new clients in different languages if they think we’ve done a bad job.
Second, we sign all updates to the Keybase reference client, and
provide an update mechanism
to download new clients without trusting HTTPS, only the integrity
of our key. We keep that private key offline, so that it wouldn’t be compromised
in the case of a server compromise.
We fully understand that users of the Keybase Web client don’t get these guarantees.
But our hope is that enough users will use the Keybase command-line client
to keep the Web users safe, by catching server misbehavior in the case of a
compromise.
Копирование идентификатора
Самые простые системы Mifare можно взломать, сделав дубликаты ключей. SMKey отлично подойдет для такой цели. Копирование ключей Mifare происходит следующим образом:
- Копировальщик делает дубликаты меток с закрытыми отделами.
- Полученные данные после используются для переноса на заготовки под ключ, заменяющие оригинальные брелоки.
Процесс копирования
Изначально на основании всей информации из считывателя рассчитывается криптоключ. Mifare-ключи не нужно подбирать, поэтому процесс осуществляется гораздо быстрее чем обычно. При помощи программы производится копирование основных меток MF Classic 1K и Ultralight. Частота выполнения процедуры составляет 13,56 МГц.
Метки MF Classic копируются, после чего программа-дубликатор брелоков от домофона Mifare записывает все полученные данные на заготовленный брелок. MF Zero и MF OTP считаются самыми популярными моделями для заготовок. Они позволяют однократно записать UID, благодаря чему можно обходить фильтры систем считывание идентификационных данных Iron Logiс. Дублированные метки Ultralight переписываются на заготовки типа MF UL.
Вся дублированная база данных может храниться на пользовательском компьютере с целью создания следующих дубликатов ключей. Это делается при помощи особой программы iKeyBase, работающей под основными операционными системами.
Sibkeys
A Keybase account can have any number of sibling keys (called sibkeys) which can all sign links. This is different from PGP, which has a “master key” that you’re expected to keep tucked away in a fireproof safe — because if you misplace a device that has a copy of it, your only option is to revoke the whole key and start from scratch. We discuss this problem in a blog post.
You add and remove sibkeys by adding links to your sigchain. Since every link is checked against the state of the account at that point in the sigchain, old links remain valid even if their signing keys are revoked later. Revoking a key doesn’t affect your identity proofs, other keys, or followers.
Team features
Teams can be what we call , , or . Each has different features and abilities.
Big teams
Organize chats in channels.
If you create channels for a chat, your team becomes a big team. It doesn’t matter how many people are in it; even two people can be a big team.
Channels are a way to organize chats. They’re useful for focusing conversations on a specific project or idea but they’re not private. Everyone on a team can search and read all messages and files shared in any and every channel. To share private messages or files, you need to .
Subteams
A subteam is a private group created within a team. A subteam can include members of a team as well as people who are not a part of that team.
For example, an organization may want to create a subteam for a hiring committee. The hiring committee subteam could include team members as well as board members that aren’t a part of the team.
In a subteam, you can share private chats and files within a team. Only members of the subteam can read them. And while teams are public (outsiders may see that they exist but can’t necessarily see who is in them), subteams are stealthy. People who aren’t in them can’t even see that they exist.
Just like any other team, a subteam becomes a big team when you add chat channels. But permissions and roles work a little differently:
- Only team owners and admins can make subteams.
- Subteams do not have owners.
- Subteams may have “implicit admins,” people who are admins of the parent team but not of this subteam. Implicit admins do not have access to files and messages shared within a subteam, but they can add themselves to the subteam and gain access.
- When implicit admins add anyone (including themselves) to a team, it is announced to the other members.
Open teams
Build community.
Anyone can join an open team. So, if you’re building a community, you might want to make an open team. You can also let Keybase know about it and we may be able to help get the word out.
If you know of an open team you’d like to join, for example or , you can select to request being added. Since you can’t necessarily see who’s on a team, Keybase pings the admin for you. The admin can accept or ignore your request.
Команды
Keybase запустил «команды» — функцию аналогичную Slack. Команды могут быть разделены на «подгруппы». Например, будет подгруппой из , а будет подгруппой из (и, следовательно, также из ).
Администрирование групп
Команды управляются с помощью добавления подписей в цепочку. Каждая подпись может добавлять, удалять или изменять членство пользователя в группе. Каждая цепочка начинается с подписи владельца команды, с последующими действиями, подписанными администраторами группы или пользователями. Это гарантирует, что каждое действие производится авторизованным пользователем, и, что действия могут быть проверены любым лицом.
Decrypting & verifying
Decrypting and verifying are slightly more complicated than encrypting or signing,
because often, you don’t know ahead of time which KeyManagers are required.
For PGP messages that are signed and encrypted, you only know
which verification key is needed after a successful decryption.
Also, messages in PGP can be encrypted for multiple
receivers, and any given receiver might only have access to one of many possible decryption keys.
In kbpgp, the function handles the nitty-gritty of decryption and
verification. You need to pass it a PGP message (encrypted, signed or both), and also a way
to fetch keys midstream — a object. You can use one of ours
out-of-the-box or subclass your own (say, if you want to fetch keys from your server).
Out-of-the-Box: The KeyRing
The first example of a KeyFetcher we’ll consider is a KeyRing — a object that you can load
ahead of time with a bunch of KeyManagers.
ring = new kbpgp.keyring.KeyRing
kms =
for km in kms
ring.add_key_manager km
var ring = new kbpgp.keyring.KeyRing();
var kms = ;
for (var i in kms) {
ring.add_key_manager(kms);
}
CoffeeScript
For convenience, the class also implements the KeyFetcher interface. If you
know ahead of time that you’ll only need one KeyManager in a decryption/verification, then you can
use it as a KeyFetcher.
Decryption and Verification Example
Decrypt and verify via the function.
Pass the message, the KeyFetcher (like above), an ASP if you intend
to cancel or monitor progress, and a callback to fire when done:
ring = new kbpgp.keyring.KeyRing
kms =
pgp_msg = "---- BEGIN PGP MESSAGE ----- ...."
asp =
for km in kms
ring.add_key_manager km
kbpgp.unbox { keyfetch : ring, armored : pgp_msg, asp }, (err, literals) ->
if err?
console.log "Problem: #{err}"
else
console.log "decrypted message"
console.log literals[].toString()
if (km = literals[].get_data_signer()?.get_key_manager())?
console.log "Signed by PGP fingerprint"
console.log km.get_pgp_fingerprint().toString('hex')
var ring = new kbpgp.keyring.KeyRing;
var kms = ;
var pgp_msg = "---- BEGIN PGP MESSAGE ----- ....";
var asp = ;
for (var i in kms) {
ring.add_key_manager(kms);
}
kbpgp.unbox({keyfetch: ring, armored: pgp_msg, asp }, function(err, literals) {
if (err != null) {
return console.log("Problem: " + err);
} else {
console.log("decrypted message");
console.log(literals[].toString());
var ds = km = null;
ds = literals[].get_data_signer();
if (ds) { km = ds.get_key_manager(); }
if (km) {
console.log("Signed by PGP fingerprint");
console.log(km.get_pgp_fingerprint().toString('hex'));
}
}
});
CoffeeScript
calls back with two arguments: an Error if something went wrong, and an array
of if not. objects support the
and methods. The former call takes an optional parameter which is an encoding;
if none is supplied, kbpgp will use the encoding specified in the PGP message; you can
specify ‘utf8’, ‘ascii’, ‘binary’, ‘base64’ or ‘hex’ if you want to override that encoding.
This example shows that handles both decryption and verification. To check
if parts of the message were signed, make a call on each in the message. Note that the same KeyManager that you loaded into your KeyFetcher shows up here. So if you augment
that KeyManager with custom fields, they will be available here.
The KeyFetcher Interface
In a more general decryption/verification scenario, you might need to fetch the appropriate
decryption and/or verification keys from secondary or remote storage. In this situation, you
shouldn’t use the KeyRing described above, but should instead provide a custom KeyFetcher.
All usable KeyFetchers must implement one method: . Given several
PGP key IDs, and a flag specifying which operation is requested, the fetch method should
call back with a , if it could find one.
is called with three arguments:
- ids — An array of Buffers, each one containing a 64-bit ID of a PGP key.
These keys might refer to subkeys, which are often employed in encrypting and signing
messages. -
ops — Which crypto options are required of this key; a bitwise OR of
constants from , which are:- encrypt : 0x1
- decrypt : 0x2
- verify : 0x4
- sign : 0x8
-
cb — A callback that when done, calls back with a triple:
- err is an Error explaining what went wrong, or on success.
- km is, in the case of success, a KeyManager that meets the given requirements
- i is, in the case of success, an integer indiciating which of the keys
was found in the lookup. If is returned here, then is
the 64-bit ID of a key inside .
We’re just getting started with this tutorial and examples. Hit us up on github
if anything is missing.