Программное обеспечение мониторинга сетевого трафика для всестороннего анализа трафика
Содержание:
- MikroTik Netflow Monitoring
- Как пользоваться wireshark для анализа трафика Austin Brooks
- Summary
- Why NetVizura NetFlow Analyzer?
- Generate real-time traffic reports and closely monitor the monthly traffic trend.
- NetFlow Analyzer 11.0
- Архитектура NetFlow
- + Steps for Upgrade from BUILD 9900/10000/10100/10200 to BUILD 10250
- DIY NetFlow Analyzer Solutions
- RoMON
- NetFlow Analyzer security options
- What is a NetFlow Analyzer
- NBAR
- History of Netflow
- General
- Examples
- What Is NetFlow?
- Five other ways NetFlow Analyzer stands out above the competition
- NetFlow Analyzer 12.1
- NetFlow Analyzer 10.2.5
- NetFlow vs. sFlow
MikroTik Netflow Monitoring
Looking for more MikroTik NetFlow support or how to configure other network devices for NetFlow reporting and network visibility? Please comment below if you have any questions or came across any issues configuring your MikroTik Router, or reach out to our support line at 207-324-8805 x4.
Austin Brooks
Austin is a QA Engineer in the R&D department at Plixer. He works on new report types and aids the front end team with changes to the user interface of Scrutinizer. He has worked in Tech Support as well as a Solutions Engineer for the sales team at Plixer before his move to Development. Austin graduated from UNH’s WSBE with a degree in International Business and speaks a bit of German. Outside of work, Austin spends his time honing his coding skills and does website design for friends and family. He enjoys skiing, hockey, playing and writing music as well as traveling to different countries.
Summary
Sub-menu:
MikroTik Traffic-Flow is a system that provides statistic information about packets which pass through the router. Besides network monitoring and accounting, system administrators can identify various problems that may occur in the network. With help of Traffic-Flow, it is possible to analyze and optimize the overall network performance. As Traffic-Flow is compatible with Cisco NetFlow, it can be used with various utilities which are designed for Cisco’s NetFlow.
Traffic-Flow supports the following NetFlow formats:
- version 1 — the first version of NetFlow data format, do not use it, unless you have to
- version 5 — in addition to version 1, version 5 has possibility to include BGP AS and flow sequence number information. Currently RouterOS does not include BGP AS numbers.
- version 9 — a new format which can be extended with new fields and record types thank’s to its template-style design
Why NetVizura NetFlow Analyzer?
More than bandwidth monitoring
Why stop at bandwidth consumption monitoring when you can have more?NetVizura is a powerful analytic tool that gives your network team more information: extensive flow records with no archive size limit, flow and packets charts in addition to standard bits charts to name a few. Boost your capacity to troubleshoot faster and increases your network security in addition to bandwidth monitoring!
More visibility with less NetFlow routers
NetVizura allows you to enable NetFlow export on just a few routers and still get network-wide traffic statistics segmented into IPsubnets that represent departments and remote offices.
Simple pricing
NetVizura NetFlow Analyzer license is based solely on the flow rate of your network.There are no limitations to the number of NetFlow routers, interfaces, hosts or users.
Custom traffic monitoring
Why monitor just interface traffic when you can monitor any traffic?NetVizura allows you to define custom traffic to be monitored based on IP subnets and traffic characteristics like protocol and service used. Monitor specific traffic for each organisational unit in your network such as departments, remote sites and collections of regional offices by identifying them with IP subnets.
No NetFlow capable device? No problem!
Get full statistics without any NetFlow capable device by installing a free software for NetFlow capture and export.Traffic will be separated into different segments by IPsubnets and monitored viaTraffic Patterns.
Generate real-time traffic reports and closely monitor the monthly traffic trend.
You can start analyzing your traffic data with most intuitive bandwidth reports in Network Traffic Analyzer. Consolidated reports show you overall traffic statistics for each WAN link. Using this network traffic analysis system, you can view current traffic patterns, along with details on hosts, applications, and conversations generating traffic. Also, with reporting you can analyze network traffic trends to identify peak usage hours, link utilization metrics, and more. NetFlow analyzer also performs in-depth network packet analysis to give you a holistic view of application usage, protocol usage, and other utilization trends.
NetFlow Analyzer 11.0
-
Application-level traffic shaping capabilities: NetFlow Analyzer can now reconfigure its QoS policies with traffic shaping techniques, to ensure critical business apps are served on priority. It allows to shape traffic via ACL or class-based policies(Service Policy) to gain control over the applications consuming unwanted bandwidth. Shaping bandwidth is also done at interface and router level.
-
ACL configuration for CISCO IOS device:Access control list can be viewed at device, interface and Layer 4 apps page to filter IP packets based on source & destination address rule. If there is a match in one of the access list statements, the ACL either permits/deny the traffic.
-
CBQoS configuration for CISCO IOS device: This feature allows to create new class with «match statement» and «match criteria» and apply policy to the created class from the web GUI itself. It also allows to delete or modify the existing policy. Service Policy can be viewed from Devices, Interface, Layer4 apps & Layer7 apps and QoS page along with Preview option.
-
One click flow export: «Add devices» facility from the NetFlow Analyzer, lets users to discover routers and switches and configure them to export flows from the web console itself— in just a single click. This reduces the energy to export it manually from devices and saves time.
-
Alert profile configuration for attacks: Now it is possible to create email and SMS notifications for DoS attacks. Add alert configuration from settings and generate alerts which satisfy defined criteria, thus notifying users about attacks in real time.
- QoS level configuration: DSCP value can be configured to classify the traffic and shape it to ensure high priority for business critical apps.
Архитектура NetFlow
Netflow предоставляет возможность анализа сетевого трафика на уровне
сеансов, делая запись о каждой транзакции TCP/IP.
Информация не столь подробна, как предоставляемая tcpdump’ом,
но представляет довольно подробную статистику.
Netflow имеет три основых компонента:
- сенсор;
- коллектор;
- система обработки и представления данных.
Сенсор — демон, который слушает сеть и фиксирует
данные сеанса. Также как Snort или любая другая система обнаружения вторжений,
коллектор должен иметь возможность подключиться к хабу, «зеркалированному» порту
коммутатора или любому другому устройству, для просмотра сетевого
трафика. Если вы используете систему пакетной фильтрации на базе BSD
или Linux, то это превосходное место для коллектора Netflow, так как
весь трафик будет проходить через эту точку. Сенсор будет собирать
информацию о сеансах и сбрасывать ее в коллектор.
Коллектор — второй демон, который слушает на UDP порту, указанному
вами и осуществляет сбор информации от сенсора. Полученные данные он
сбрасывает в файл для дальнейшей обработки. Различные коллекторы
сохраняют данные в различных форматах.
Наконец, система обработки читает эти файлы и генерирует отчеты в
форме, более удобной для человека. Эта система должна быть совместима
с форматом данных, предоставляемых коллектором.
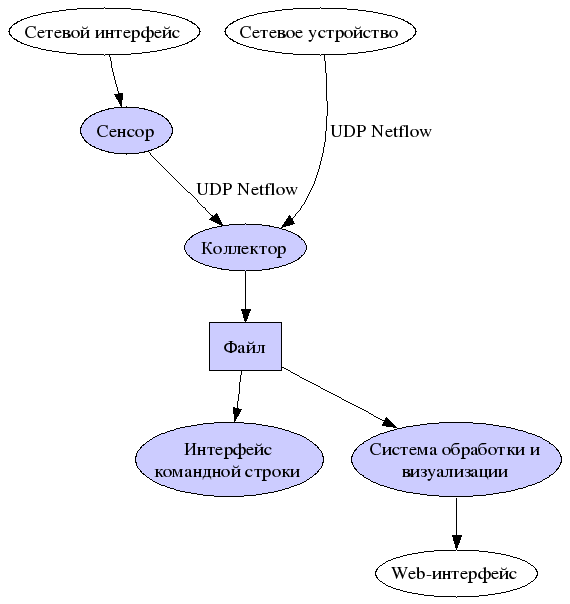
В качестве каждого из элементов системы
может использоваться несколько разных вариантов программ.
Список доступного программного обеспечения, предназначенного для работы
с NetFlow приведен .
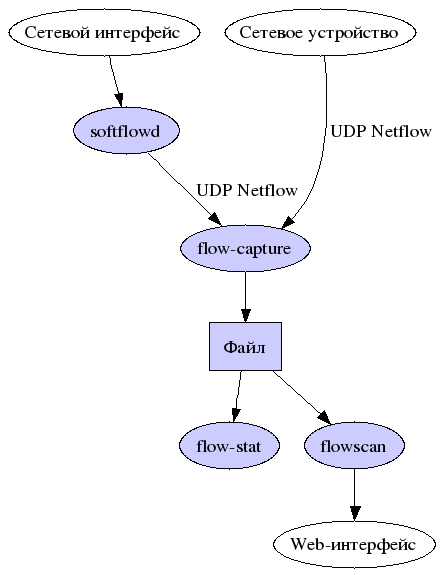
Мы рассмотрим свзяку:
- softflowd в качестве сенсора
- flow-capture (из комплекта flow-tools) в качестве коллектора
- flow-stat (из комплекта flow-tools) для анализа в текстовой строке
- flowscan для визуализации и представления в Web
+ Steps for Upgrade from BUILD 9900/10000/10100/10200 to BUILD 10250
Download the service pack from the link given below and follow the instructions:
NOTE: Ensure you are on BUILD 9900 or above as the service pack can be applied only on top this BUILD.
- Shut down NetFlow Analyzer. If NetFlow Analyzer is running as a service, stop the service also.
- Navigate to <NetFlow_Home troubleshooting>. Execute «rawCleanup.bat» for Windows and «rawCleanup.sh» for Linux.
- Copy the directory to a safe location. Note : This version involves JRE upgrade, Please follow the Step 4 without fail:
- Download the JRE upgrade pack by clicking on Relevant NetFlow installation and copy the same to (NetFlow\) directory: Note: To find the Installation, navigate to NetFlow_Home/jre/bin in a command and execute java -version for Window or ./java -version for Linux. If its is 64 bit 64-bit will be displayed in the output else its a 32 bit installation
- 32 Bit Windows OS
- 64 Bit Windows OS
- 32 Bit Linux OS
- 64 Bit Linux OS
- Execute the UpdateManager.bat (.sh in case of Linux) file present in the /bin directory.
- From the window that pops up, click Browse and select the service pack you downloaded.
- Click Install to install the service pack. This may take several minutes depending on the amount of data that needs to be migrated.
- Wait until the service pack is fully installed.
- Click Close and then click Exit to exit the Update Manager tool.
- Start the NetFlow Analyzer service.
DIY NetFlow Analyzer Solutions
For whatever reason, sometimes pre-packaged tools can’t give you what you need. Maybe they’re not powerful enough. Maybe you’re a highly knowledgeable IT professional and think you could build something better than what’s out there, or just want to try your hand at homegrown NetFlow data analysis. Whatever the case may be, options are available for those looking to create their own solution for NetFlow monitoring and analysis.
Splunk, Elastic Stack, and Grafana are a few examples of software you can use to build a decent traffic analysis system. Splunk is a packet sniffer offering a NetFlow add-on, and Elastic Stack and Grafana are open-source toolsets capable of integration with NetFlow. The success of the do-it-yourself approach depends on the current size of your network, how complex it is, and how big you expect it to grow in the future, as well as your level of expertise—including whether you’re willing to put in the time and effort to learn.
RoMON
RoMON – утилита для доступа к устройствам через MikroTik находящихся в одном l2 сегменте с пограничным устройством, к которому у нас есть прямой доступ. Находится в /tool RoMON, помогает при удаленном администрировании.
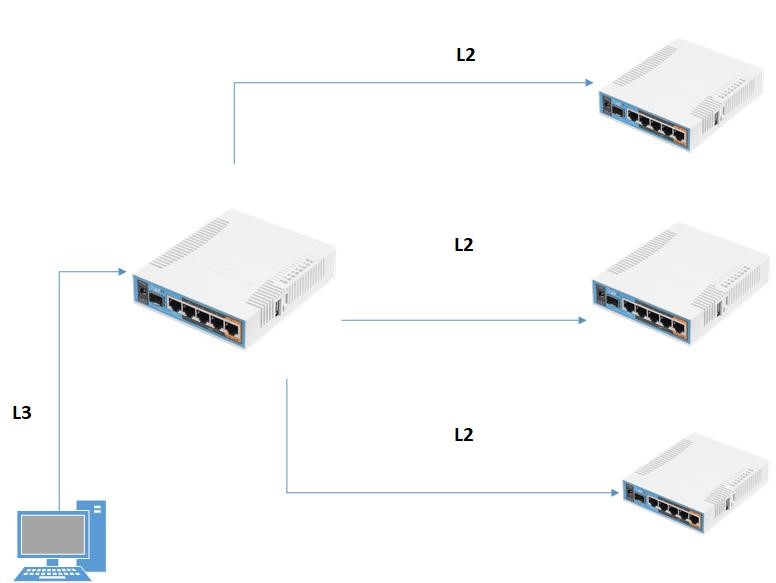
Этот инструмент удобно использовать, когда по каким-либо причинам нам не хочется для настройки новых устройств за роутером использовать CLI (Mac Telnet) а хочется все делать через winbox.
Для использования этой функции нужно ее активировать как на роутере, к которому у нас есть доступ так и на тех (через Mac Telnet) которые находятся за нашем устройством. Включается оно /tool RoMON.
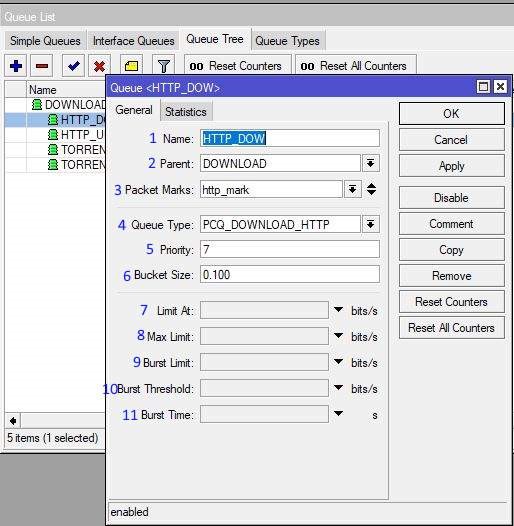
NetFlow Analyzer security options
In general, NetFlow Analyzer software is an essential part of any security infrastructure for detecting anomalies in the network and troubleshooting threat incidents. It compliments firewalls, centered on end points of the network, by providing inside view of the network. Unlike signature-based anti-viruses, facing known threats, this concept of not-preventing but quick-reacting is necessary for rising zero-day attacks. Further analysis of SIEM events can be explored thanks to NetFlow data. And, you also have a historic data archive for later investigation whenever deemed necessary. This way, it actually covers the most critical threats that network face nowadays, such as advanced persistent threats, inside threats, and even employee abuse, unauthorized access and data leak cases.
Customer Stories
«Different scanning and reconnaissance attacks coming from outside or inside of our network
can be easily detected on NetVizura NetFlow Analyzer traffic Graphs. Denial-of-Service attacks,
virus or worms activities can also be withheld with a timely detection.»
What is a NetFlow Analyzer
NetFlow is a push technology. In other words, when it is enabled on a router, switch or server, it sends a steady stream of flow information to the destination which is typically one or more NetFlow collectors. In contrast, packet analysis is a passive technology where the device listens on a spanned port and slurps in the packets for real time capture and observation. SNMP on the other hand is a polling technology where the poller asks for information from the devices every few minutes or seconds. The efficiency of one technology over another is debatable and not going to be broached in this post. However, the skillset needed to trend and report on the data for network traffic analysis is where we need to focus.
- Packet capture and analysis at scale requires expert knowledge on how to ingest hundreds of millions of packets per second, saving them and making them available for reporting in a timely manner. It is one thing to collect the data but, allowing the user to query it and mine for what they are looking for quickly requires specialization and serious database forethought.
- SNMP polling and analysis at scale requires expert knowledge on how to query tens of thousands of devices for both similar and unique object identifiers (OIDs). Fast retrieval is generally easier than packet capture but, managing the sheer volume of devices in a scalable way takes considerable time to engineer.
- NetFlow collection and analysis at scale requires a very well thought out database architecture which can shard the data to multiple servers, allow for distributed collector queries and provide the stitching and deduplication that is often requested across the entire architecture. Reporting speed for most vendors is a major problem.
A NetFlow Analyzer is a solution that collects flows, monitors them for unwanted traffic patterns and provides fast reporting with very flexible filtering. Ultimately, the customer needs to be made aware of a problem fast and be given the ability to narrow in on the source of the enigma without delay. BUYER BEWARE: most vendors claim these capabilities and only a good stress test with a heavy prolonged volume of flows will separate the NetFlow add-on module vendors from the truly dedicated to the flow industry specialists.
NBAR
-
Which features are not supported by NBAR ?
The following features are not supported by NBAR:- More than 24 concurrent URLs, HOSTs or MIME type matches
- Matching beyond the first 400 bytes in a URL
- Non-IP traffic
- Multicast and other non-CEF switching modes
- Fragmented packets
- Pipelined persistent HTTP requests
- URL/HOST/MIME/ classification with secure HTTP
- Asymmetric flows with stateful protocols
- Packets originating from or destined to the router running NBAR
Any restrictions on where we can configure NBAR?
You can’t configure NBAR on the following logical interfaces:
- Fast EtherChannel
- Interfaces that use tunneling or encryption
- VLANs
- Dialer interfaces
- Multilink PPP
Note: NBAR is configurable on VLANs as of Cisco IOS Release 12.1(13)E, but supported in the software switching path only.
What Does NBAR Performance Depend On?
Several factors can impact NBAR performance in software-based execution.
A. Router Configuration
1. Number of protocols being matched against it
2. Number of regular expressions being used
3. The complexity of packet inspection logic required
B. Traffic Profile (Packet Protocol Sequence)
1. The number of flows
2. Long duration flows are less expensive than shorter duration flows
3. Stateful protocol matches are more performance impacting than static port applications
Is performance dependent on the number of interfaces that NBAR is enabled on? Does the link speed of the interface(s) that NBAR is enabled on affect performance ?
No. NBAR performance is not dependent on the number of interfaces that NBAR is enabled on or the link speed of those interfaces. Performance is dependent on the number of packets that the NBAR engine has to inspect, how deep into the packet it has to look to perform regular inspection.
I am able to issue the command «ip nbar protocol-discovery» on the router and see the results. But NFA says my router does not support NBAR, Why?
Earlier version of IOS supports NBAR discovery only on router. So you can very well execute the command «ip nbar protocol-discovery» on the router and see the results. But NBAR Protocol Discovery MIB(CISCO-NBAR-PROTOCOL-DISCOVERY-MIB) support came only on later releases. This is needed for collecting data via SNMP. Please verify that whether your router IOS supports CISCO-NBAR-PROTOCOL-DISCOVERY-MIB.
How do I verify whether my router supports CISCO-NBAR-PROTOCOL-DISCOVERY-MIB?
a) You can check CISCO-NBAR-PROTOCOL-DISCOVERY-MIB supported platforms and IOS using the follwoing link. http://tools.cisco.com/ITDIT/MIBS/AdvancedSearch?MibSel=250073
b) Alternately , you can execute «show snmp mib | include cnpd » command at router to know the implemeted mib objects in the router. If the router supports CISCO-NBAR-PROTOCOL-DISCOVERY-MIB, then the above command gives the following objects.
cnpdStatusEntry.1
cnpdStatusEntry.2
cnpdAllStatsEntry.2
cnpdAllStatsEntry.3
cnpdAllStatsEntry.4
cnpdAllStatsEntry.5
cnpdAllStatsEntry.6
cnpdAllStatsEntry.7
cnpdAllStatsEntry.8
cnpdAllStatsEntry.9
cnpdAllStatsEntry.10
cnpdAllStatsEntry.11
cnpdAllStatsEntry.12
cnpdTopNConfigEntry.2
cnpdTopNConfigEntry.3
cnpdTopNConfigEntry.4
cnpdTopNConfigEntry.5
cnpdTopNConfigEntry.6
cnpdTopNConfigEntry.7
cnpdTopNConfigEntry.8
cnpdTopNStatsEntry.2
cnpdTopNStatsEntry.3
cnpdTopNStatsEntry.4
cnpdThresholdConfigEntry.2
cnpdThresholdConfigEntry.3
cnpdThresholdConfigEntry.4
cnpdThresholdConfigEntry.5
cnpdThresholdConfigEntry.6
cnpdThresholdConfigEntry.7
cnpdThresholdConfigEntry.8
cnpdThresholdConfigEntry.9
cnpdThresholdConfigEntry.10
cnpdThresholdConfigEntry.12
cnpdThresholdHistoryEntry.2
cnpdThresholdHistoryEntry.3
cnpdThresholdHistoryEntry.4
cnpdThresholdHistoryEntry.5
cnpdThresholdHistoryEntry.6
cnpdThresholdHistoryEntry.7
cnpdNotificationsConfig.1
cnpdSupportedProtocolsEntry.2
History of Netflow
As mentioned previously, Netflow was conceived at Cisco Systems, and is now a major standard that is included in almost every business grade router and switch that Cisco and other manufacturers produced.
Prior to Netflow, Network engineers and Administrators relied primarily on SNMP (Simple Network Management Protocol) to monitor network and internet traffic on their LAN and WAN connections.
SNMP is great for monitoring networked devices and capacity planning, but it lacks in more granular and in-depth traffic and bandwidth usage and utilization.
Roland Dobbins, a network engineer in the Internet Services group at Cisco said, “We needed a more granular understanding of how Cisco bandwidth is used,”.
Soon after, Cisco introduced its Netflow Technology in 1996 which allowed for deeper insight, characterization and the ability to further analyze network traffic flows using a specialized Application-Specific Integrated Circuit (ASIC) coupled with features within the Cisco IOS Firmware and Catalyst OS Software.
By 2003, Cisco’s Netflow Version 9 would be chosen to become a IETF (Internet Engineering Task Force which proposes Standards for the Internet, primarily TCP/IP) standard formally called IPFIX, or IP Flow Information Export.
For additional Reading on What Netflow is and How you can use it to monitor and analyze your Network, check out the following Whitepapers for more in-depth reading:
General
Sub-menu:
This section lists the configuration properties of Traffic-Flow.
| Property | Description |
|---|---|
| interfaces (string | all; Default: all) | Names of those interfaces which will be used to gather statistics for traffic-flow. To specify more than one interface, separate them with a comma. |
| cache-entries (128k | 16k | 1k | 256k | 2k | … ; Default: 4k) | Number of flows which can be in router’s memory simultaneously. |
| active-flow-timeout (time; Default: 30m) | Maximum life-time of a flow. |
| inactive-flow-timeout (time; Default: 15s) | How long to keep the flow active, if it is idle. If connection does not see any packet within this timeout, then traffic-flow will send packet out as new flow. If this timeout is too small it can create significant amount of flows and overflow the buffer. |
Note: Starting 6.0rc14 release setting interface will show RX and TX for the interface. Previously traffic-flow reported only RX fraffic for the interface and to see bidirecional data it was required to set up more interfaces.
Examples
This example shows how to configure Traffic-Flow on a router
Enable Traffic-Flow on the router:
ip traffic-flow> set enabled=yes
ip traffic-flow> print
enabled: yes
interfaces: all
cache-entries: 1k
active-flow-timeout: 30m
inactive-flow-timeout: 15s
ip traffic-flow>
Specify IP address and port of the host, which will receive Traffic-Flow packets:
ip traffic-flow target> add dst-address=192.168.0.2 port=2055 version=9 ip traffic-flow target> print Flags: X - disabled # SRC-ADDRESS DST-ADDRESS PORT VERSION 0 0.0.0.0 192.168.0.2 2055 9 ip traffic-flow target>
Now the router starts to send packets with Traffic-Flow information.

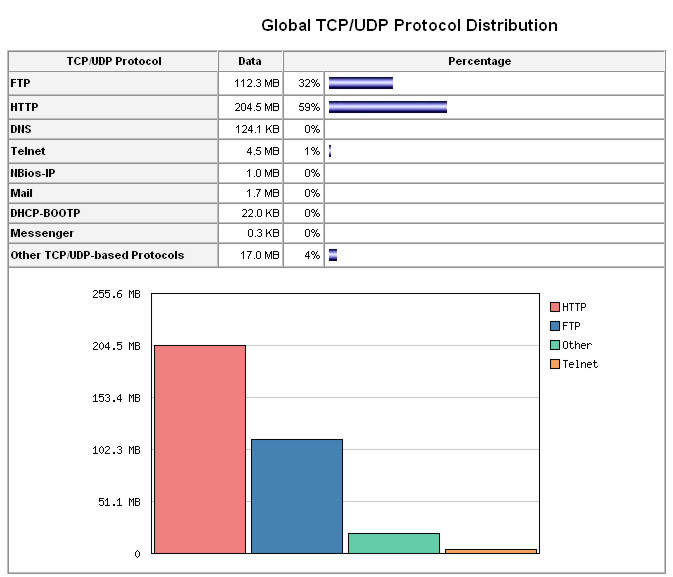
What Is NetFlow?
Every experienced IT professional knows a comprehensive view of your network is critical. As technology rapidly advances, challenges have arisen in understanding network behavior, particularly in the areas of compliance, network security vulnerabilities, network productivity and the dispersal of resources, and application usage. In 1996, Cisco released NetFlow as a network protocol to offer insight into all these areas within a cohesive operating environment.
Used to collect information about your network IP traffic and to monitor network traffic activity, NetFlow generates insights into application flows. By implementing a high-quality network performance monitor with a NetFlow reporting tool, you can troubleshoot network issues with a high level of specificity. For larger businesses with large IT departments, the information gleaned from NetFlow analysis can be used to facilitate more accurate capacity planning and decisions about how to best allocate network resources.
Information provided by NetFlow can be leveraged to address a range of issues.
- Do you have a new application on your network? NetFlow helps you isolate what’s taking a toll on your network load.
- Are you having trouble with your network? Speed up troubleshooting and get to the bottom of poor network performance.
- Have you been seeing a reduction in wide-area network (WAN) traffic? See who or what is taking up the most bandwidth in your network.
- Have you been noticing unauthorized WAN traffic? NetFlow will pinpoint the applications causing problems, so you don’t have to spend money replacing or upgrading all your software.
- Do you have a security issue? When used in tandem with other applications like Cisco CS-Mars, NetFlow can check for anomalies and worms.
- Do you need help validating the quality of service (QoS) specifications? Keep track of your bandwidth allocation to make sure you’re not overextended.
NetFlow is in its ninth version now. If you want extra power, you can download Flexible NetFlow and IPFIX extensions.
Five other ways NetFlow Analyzer stands out above the competition
Cisco Class-based Quality of Service (CBQoS) monitoring
- CBQoS is a Cisco feature set that provides information about the applied QoS policies and class-based traffic patterns within an enterprise’s network.
- The report shows the pre-policy and post-policy drops in traffic within the network.
- These policies can be changed based on these reports in NetFlow Analyzer, which can also be used for QoS policy validation.
Network Based Application Recognition (NBAR)
- NBAR is an intelligent classification engine that can monitor, recognize, and intelligently identify a wide variety of applications that use dynamic ports.
- NetFlow Analyzer now uses NBAR2 to analyze and classify application traffic in real time. The NBAR2 reports show the list of applications that are identified with NBAR2 along with their traffic details and the contribution of a particular application’s traffic to the total traffic in the network.
Cisco AVC monitoring
- The number of business and other applications that use HTTP is increasing everyday, and as a result, identifying applications by checking the well-known ports is no longer sufficient.
- The need for application visibility in the network is on the rise and NetFlow relies on Cisco Application Visibility and Control (AVC) technology, that provides application-level classification for application categorization to obtain the required visibility.
IP service-level agreement (SLA) monitoring
- Cisco IP SLA is technology from Cisco that actively monitors traffic to measure the performance of the network by measuring critical parameters of the network.
- In addition, vital factors like jitter, latency, packet loss, and mean opinion score (MOS) are also measured.
Medianet Reporting
- Cisco Medianet is an intelligent network optimizer made for media-rich traffic to enhance user experience.
- It enables the network to optimally perform despite having bandwidth-consuming-rich-media traffic in it.
- Accelerate troubleshooting in your media-rich network, and save time, money, and more.
With more features and updates on the way, now’s the best time to take the NetFlow Analyzer for a test drive. Click here to download a 30-day free trial.
NetFlow Analyzer 12.1
-
New easy-to-use web client for both editions: NetFlow Analyzer has made navigation between tabs even more easier with greater visibility and control over network data and thus, makes it more reliable and user friendly.
-
High Scalability:NetFlow Analyzer Essential & Enterprise edition (each collector) can now scale upto 100k flows/sec.
- Network configuration manager add-on to manage all the configuration changes along with change management & compliance management has been added to both the editions.
-
Tight integration with network management solution: This enhancement has brought bigger benefits by managing your entire network infrastructure with single exe for all the available softwares by availing very tight integration with ManageEngine OpManager.
-
Wireless LAN Controller monitoring: This feature is now available as add-on to take control of your wireless APs and LANs for better management of enterprise bandwidth.
-
End User Bandwidth monitoring: Introducing this feature as BETA to monitor end-users bandwidth usage which has enhanced the way of troubleshooting excessive bandwidth usage better.
-
Collaboration tool added: Group chat is now available at free of cost to interact within teams to resolve/assign the issues in more simplified way. Alerts can be discussed with the help of this tool.
- Newly added settings for Network Mapping: Now you can create visual view of network maps with the help of this setting and add network devices and priority links to get live status of your network links.
NetFlow Analyzer 10.2.5
-
Heat Maps: Heat maps in NetFlow Analyzer helps to visualize the health status of all the interfaces in a single page. It uses color codes to depict the severity of the monitored devices.
-
QoS graphs:QoS graphs displays the real-time information of interface traffic in graphical format. This helps to get a better view of your interfaces and applications performance.
- API Client Enhancements: This release includes various enhancements to the existing UI such as add & edit options included in IP Groups, Interface Groups & Alert Profiles, add option included in DSCP & App Groups, option to add, edit & delete User Management, new segment named «Attacks» added inside Settings comprising of ASAM Setting, manage Config, and threshold Setting.
Note: All the above mentioned features are available in Essential and Large Enterprise Editions. For Enterprise Edition, this release is just incluces the scalability enhancements that got released in 10.2.
NetFlow vs. sFlow
Be careful not to confuse NetFlow with sFlow. While both are concerned with packets and network traffic, NetFlow uses templates, while sFlow is a NetFlow alternative using protocol extensions rather than templates.
Going into more depth, sFlow is a packet sampling protocol specially designed to handle high-speed or high-performance networks. The “s” stands for “sampling,” but the “flow” part of the name is a bit of a misnomer—sFlow only deals with packets, not IP flows, and those packets aren’t consolidated into flows like they are in NetFlow.
SFlow can be retrofitted to snap into any network monitoring device. The sFlow exporter will take stock of all the packets going through a device and pluck out one of every n packets, where n equals the sample rate chosen in the settings. It will supplement those samples with other randomly chosen packets. SFlow takes the bytes from these samplings, transforms them into sFlow datagrams, and sends them off to the sFlow collector.
Practically speaking, there are four major differences between NetFlow and sFlow.
- Scalability. Some say NetFlow is more accurate than sFlow because it accounts for all the packets on the network instead of just a few. However, the sFlow sampling method makes it more scalable than NetFlow because it can handle large amounts of traffic more quickly. That said, the Sampled NetFlow extension can be added to NetFlow to make it more scalable.
- Performance. NetFlow uses your system’s CPU and RAM to run the flow cache, which is good for comprehensibility but not so good for performance at high volumes. Since sFlow doesn’t deal with the network device much at all, this isn’t a problem.
- Coverage. NetFlow interacts with IP only, although some layer 2 capability has been added recently. In contrast, sFlow covers layers 2 through 7.
- Latency. With NetFlow, latency can be higher than with sFlow. NetFlow analyzers conduct flow cache exports every so often based on active and inactive timeouts, and reports can be delayed due to live traffic, especially when it comes to VoIP.
If we think of network traffic as traffic on a highway, NetFlow is a wide-lens camera capturing all the lanes, whereas sFlow takes pictures of isolated vehicles as they pass. Only NetFlow will give you a clear and all-inclusive view of your data.